The fourth industrial revolution has brought forth an era of unprecedented automation, transforming industries by enhancing productivity, driving business growth, and optimizing cost efficiency. However, as we strive to harness the power of the cloud, automation in cloud security has lagged behind.
Security teams face increasing challenges due to mounting risks, limited resources, and consequential outcomes. A more automated and reliable approach to cloud security is paramount for organizations to keep pace with the fast-evolving landscape.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

GlobalDots revolutionizes risk management with tailored automation
To navigate the complex landscape of cloud security, organizations require risk data that is trustworthy, personalized, and grounded in their specific environments. A lack of relevant information leads to time and resources being wasted on addressing “critical” risks that have no real impact.
GlobalDots steps in with an innovative automation solution that empowers organizations to take control of their vulnerability risk management programs while boosting operational efficiency. Our latest platform enhancement allows customers to obtain customized risk-based vulnerability scores without the need to handle intricate data sets or develop custom logic. The result is the elimination of monotonous tasks and reduced strain on overburdened teams.
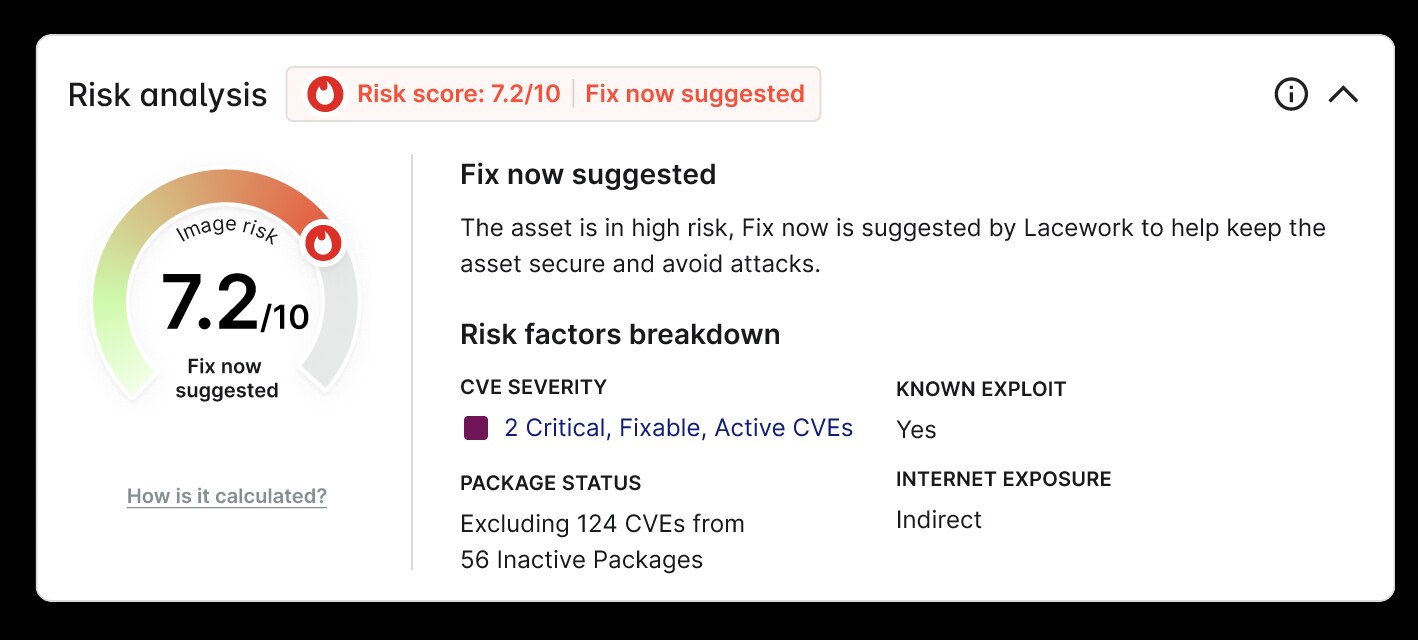
Overwhelming vulnerabilities create opportunities for breaches
Traditional risk management programs are struggling to cope with the deluge of alerts originating from cloud risks. While third-party feeds help categorize vulnerabilities based on severity, this classification is often insufficient. The National Vulnerability Database (NVD) lists over 200,000 vulnerabilities, with more than 18,000 deemed critical and 50,000 classified as high severity. In reality, severity varies depending on the unique cloud environment, vulnerability impact, likelihood of exploitation, and criticality of assets at risk.
Understaffed security teams cannot manage complex data sets or create custom manual rules to cover every risky scenario in the cloud. This resource-intensive and costly approach leaves room for error and increases the risk of data breaches.
Context is crucial for organizations to prioritize the ever-growing volume of vulnerabilities. This is where GlobalDots has a significant edge over competitors.
GlobalDots crafts custom risk-based vulnerability scores for your environment
Effective vulnerability management demands a risk-based approach that extends beyond CVSS scores and NVD-provided severity. A “critical” vulnerability for one organization may not hold the same weight for another.
GlobalDots’ CNAPP platform leverages its in-depth knowledge of your cloud environment, along with innovative research and third-party exploit data, to automatically provide custom risk-based vulnerability scores that highlight your most pressing issues.
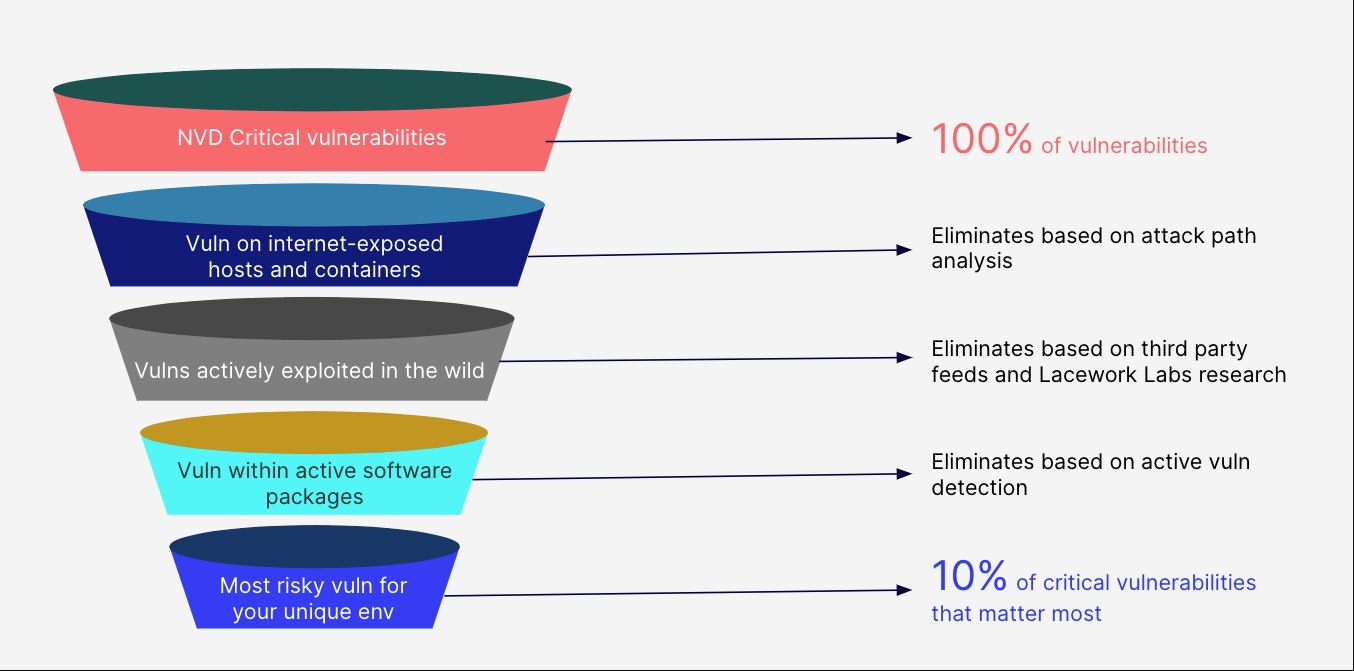
We start with the NVD to identify critical vulnerabilities, utilizing security checklists, software flaws, misconfigurations, product names, and impact metrics. We then incorporate CVE and CVSS data to assess vulnerabilities and their relative severity.
GlobalDots’ platform goes beyond by applying additional filters to critical vulnerabilities, allowing you to focus on exploitable risks. Our solution factors in unique customer attributes, active vulnerable software packages, exposure to the internet, critical data assets in the vulnerability path, and the existence of active exploits. By combining active vulnerability detection, attack path analysis, and cutting-edge research, we reduce critical vulnerabilities to a manageable number, enabling you to address your most pressing risks.
Our risk scores adjust automatically based on new cloud activity, ensuring continuous monitoring of every cloud host’s file system. The platform operates in the background, enabling you to reduce 90% of vulnerability noise effortlessly.
Active vulnerability detection ensures resources are utilized effectively
Active vulnerability detection is a core feature of our custom risk assessment. It helps to prevent wasted time and effort on fixing software that isn’t actually running and poses no security risk.
By using active vulnerability management from our agent, you can automatically identify vulnerable software packages that are active. This capability significantly cuts down on noise from inactive vulnerable packages, allowing you to refocus developer time on tasks that add value to the business.
Our customers have experienced a dramatic reduction in the number of NVD critical vulnerabilities that require remediation. This feature enables teams to concentrate on the most crucial items to fix, reducing overall risk instead of spending time on vulnerabilities that don’t truly matter.
Gain comprehensive insight into your attack paths in one centralized location
Another key component of our custom risk assessment is the attack path analysis capability. Last year, we integrated attack path analysis into our CNAPP platform. With this enhancement, every alert involving an internet-exposed vulnerability included an Exposure Visualization, illustrating how bad actors could breach and exploit data in the environment.
Our latest release takes attack path analysis even further by introducing a dedicated dashboard that provides immediate visibility into your top risks and attack paths leading to your most critical assets. This unified dashboard offers posture teams an overview of the riskiest entities in their environments, helping prioritize the most impactful work items. It also helps visualize all potential attack routes to critical data assets, giving teams an in-depth understanding of their cloud environments.
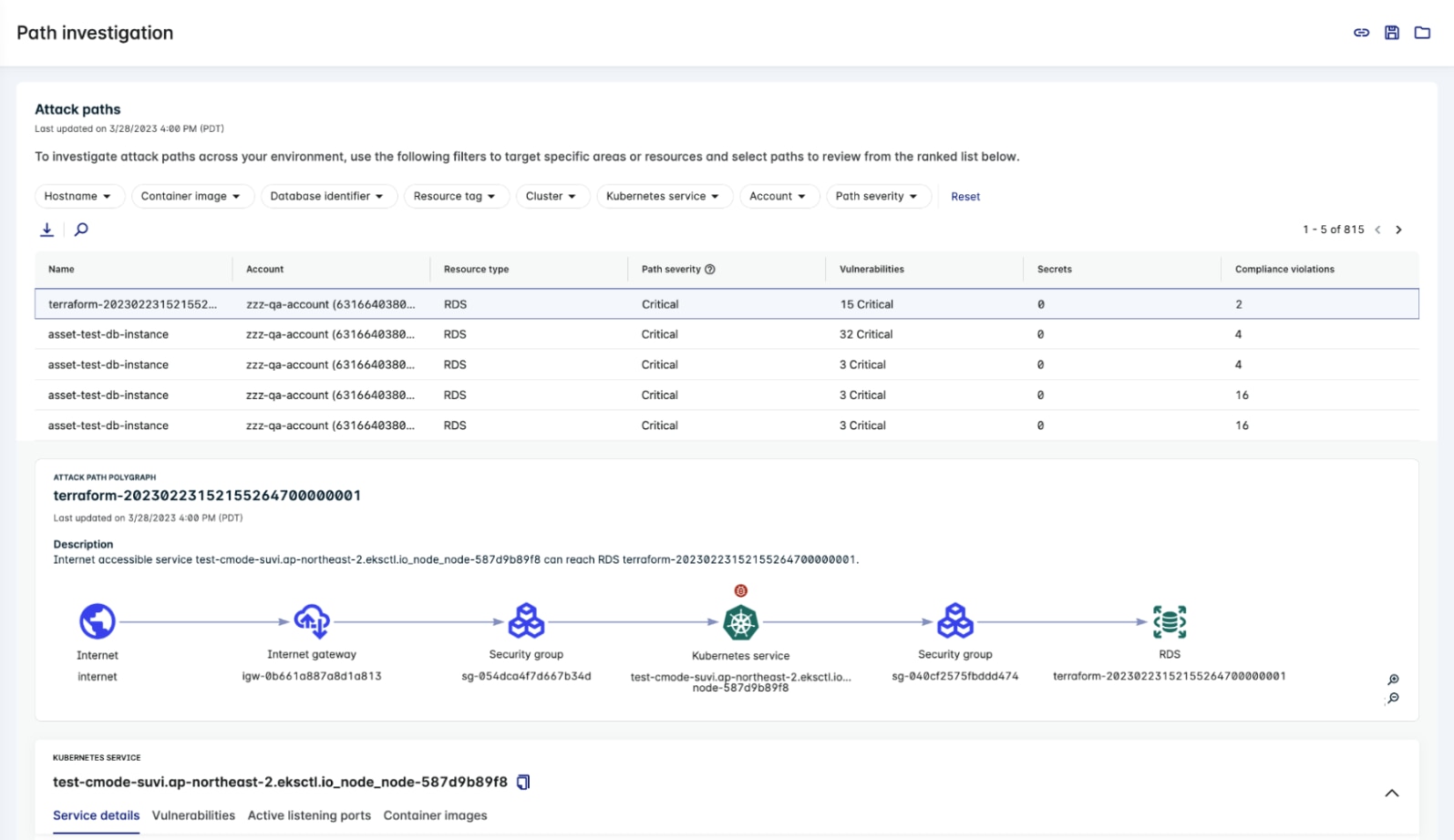
Attack paths typically start from the internet and end with an asset, such as a workload, database, or data storage device. Our latest release enables users to accurately gauge the importance of fixing an attack path risk by tracing an attacker’s steps from the internet to Amazon RDS, Amazon Aurora, and other cloud assets.
Strengthening trust between security and development teams while minimizing disruptions
With GlobalDots’ latest platform enhancements, organizations can now:
- Reduce 90% of critical vulnerability noise. GlobalDots’ CNAPP platform combines active vulnerability detection, attack path analysis, and curated exploit feeds to address 9 out of 10 critical vulnerabilities effectively.
- Customize vulnerability scores for your cloud environment. GlobalDots delivers a risk score that reflects each customer’s specific environment while allowing them to fine-tune score parameters to match their unique risk tolerance requirements.
- Distinguish between active and inactive vulnerabilities. The custom risk score reflects which vulnerable software packages are active and require immediate attention.
- Enable developers to spend more time coding and less time addressing security issues. By focusing on active vulnerabilities, developers save valuable time investigating and fixing vulnerabilities, allowing them to dedicate more time to creating value for the business.
- Foster collaboration between security and development teams. Security teams earn DevOps trust by providing developers with precise, actionable vulnerability data, ensuring that their time isn’t wasted on issues that don’t genuinely require attention.
Our intelligent automation allows security teams to efficiently manage alert queues while ensuring that development teams work on security issues that truly matter. This synergy results in a win-win situation for the numerous companies that rely on GlobalDots to protect their cloud environments every day.
To learn more about how our solutions can help protect your cloud environment and streamline vulnerability management, visit our resources hub. If you’re ready to take action, we’re offering a free consultancy and cloud security assessment to evaluate your current security posture and provide tailored recommendations.
Don’t hesitate to contact us to take advantage of this valuable opportunity and ensure your organization’s cloud security is optimized for the future.






