DNS (Domain Name System) is crucial to all organizations that rely on the Internet for conducting business – it’s critical for the performance and reliability of your internet applications and cloud services. DNS failure or poor performance leads to applications, data and content becoming unavailable, causing user frustration, lost sales and business reputation damage.
Recently, DNS hijacking attacks have become widespread. In this article we discuss DNS hijacking attacks and how you can mitigate them.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

DNS overview
Domain Name System (DNS) servers are often called “the phonebooks of the Internet” and are used to resolve human-readable hostnames into machine-readable IP addresses. They also provide other useful info about domain names, such as mail services. As when you know someone’s name but don’t know their phone number, you use phonebooks to find their number. DNS services use the same logic. When you request data for a web location you type its name and then the DNS servers find their IP address.
For example, if you request an address such as globaldots.com, DNS will translate it to something like 198.102.746.4. These internet phonebooks greatly influence the accessibility of Web locations which is exactly why DNS is crucial for any organization that relies on the Internet to connect to customers, partners, suppliers and employees.
The Internet maintains two principal namespaces, the domain name hierarchy and the Internet Protocol (IP) address spaces. The Domain Name System maintains the domain name hierarchy and provides translation services between it and the address spaces. Internet name servers and a communication protocol implement the Domain Name System. A DNS name server is a server that stores the DNS records for a domain name; a DNS name server responds with answers to queries against its database.
What is DNS Hijacking?
DNS Hijacking, also called Domain Hijacking is when bad actors redirect or “hijack” DNS addresses and reroute traffic to bogus DNS servers. Once a DNS address is successfully hijacked to a bogus DNS server, it translates the legitimate IP address or DNS name into the IP addresses of the hacker’s malicious website of choice.
DNS hijacking can be used for pharming (in this context, attackers typically display unwanted ads to generate revenue) or for phishing (displaying fake versions of sites users access and stealing data or credentials).
Many Internet Service Providers (ISPs) also use a type of DNS hijacking, to take over a user’s DNS requests, collect statistics and return ads when users access an unknown domain. Some governments use DNS hijacking for censorship, redirecting users to government-authorized sites.
DNS hijacking can occur with any size website, directing folks to malicious websites without their knowledge. Since the website owners depend upon legitimate DNS server that are issued by their Internet Service Providers (ISP), DNS hijackers use malware in the form of a Trojan to exchange the legitimate DNS server assignment by the ISP with a manual DNS server assignment from a bogus DNS server.
When users visit legitimate websites, they’re automatically hijacked to a malicious website disguised as the legitimate one. The switch from the legitimate DNS server to the bogus DNS server goes unnoticed by both the user and the legitimate website owner. At this point the malicious website gets to do pretty much anything it wants, for as long as the person using it believes it’s where they’re meant to be.
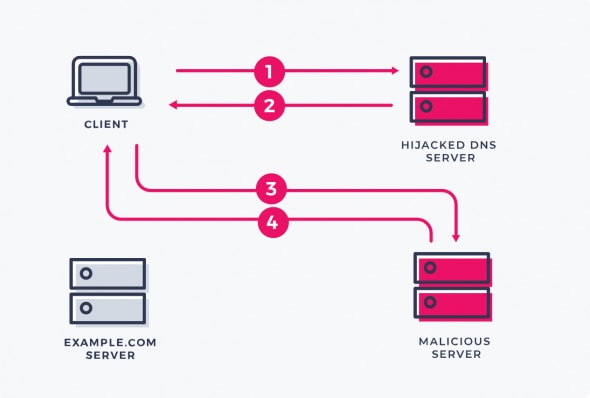
As a cyber attack, DNS Hijacking has a host of uses, including injecting malware into your machine, promoting phishing scams and advertising on high-volume websites. Ultimately, it’s possible to suffer a data breach following a DNS Hijacking, as credentials can easily be mined while the victim is active on the attacker’s bogus site.
DNS hijacking attack types
There are four basic types of DNS redirection:
- Local DNS hijack — attackers install Trojan malware on a user’s computer, and change the local DNS settings to redirect the user to malicious sites.
- Router DNS hijack — many routers have default passwords or firmware vulnerabilities. Attackers can take over a router and overwrite DNS settings, affecting all users connected to that router.
- Man in the middle DNS attacks — attackers intercept communication between a user and a DNS server, and provide different destination IP addresses pointing to malicious sites.
- Rogue DNS Server — attackers can hack a DNS server, and change DNS records to redirect DNS requests to malicious sites.
Mitigation Methods
Let’s take a look at methods you can use to prevent or mitigate DNS hijacking attacks.
Upgrade DNS in the Application Infrastructure
The lack of attention of DNS lags behind the innovation of the infrastructure in the cloud, creating cracks for possible exploitation. As organizations increasingly embrace a new generation of “cloud first” computing environments with multiple, connected clouds, data centers and CDNs, they also need to adapt and upgrade the underpinning infrastructure, including DNS and security technologies and policies.
Use DNSSEC
Application layers use security protocols (like HTTPS, DMARC, etc.), and DNS is no exception. The Domain Name System Security Extensions(DNSSEC) is one of them. DNSSEC reinforces the authenticity of DNS query responses by using digital signatures to authenticate communications, protecting applications (and the caching resolvers used by those applications) from using fake DNS data in cache poisoning and spoofing attacks.
Historically, organizations have held back from using DNSSEC, because implementing it would mean sacrificing the DNS traffic management capabilities they rely on to deliver high quality online services.
However, with recent technological developments, this is no longer a problem.
Secure access
Use two-factor authentication when accessing the DNS registrar, to avoid compromise. If possible, define a whitelist of IP addresses that are allowed to access DNS settings.
Client lock
Check if your DNS registrar supports client lock (also known as change lock), which prevents changes to your DNS records without approval from a specific named individual.
Mitigation for end users
End users can protect themselves against DNS hijacking by changing router passwords, installing antivirus, and using an encrypted VPN channel. If the user’s ISP is hijacking their DNS, they can use a free, alternative DNS service such as Google Public DNS, Google DNS over HTTPS, and Cisco OpenDNS.
Conclusion
DNS hijacking has become a serious problem for many enterprises and end users. If you want to protect your business from DNS hijacking, you should implement the mitigation methods we’ve mentioned above.
If you’re still not sure you’ll be able to mitigate various DNS hijacking attacks, contact us today to help you out with your performance and security needs.






