What is a DDoS Attack?
A DDoS – distributed denial of service is when more than one, often thousands of, IP addresses are used to make a service unavailable to its intended users. It’s like someone crowding your shop with people not to let other people in. Now, a denial of service can either crash or flood the service. The more machines involved in the attack, the harder the attack and more devices working with a uniform goal to target you, the host, with as many communication packets as possible. Now, this can:
- slow down your network performance
- make your website unable to access for days, for weeks
- spam you with e-mails dramatically
- disconnect a wireless or wired Internet connection
- cause long term denial of access to the web or any Internet service
If a server is overloaded with connections, it can no longer accept new connections. This can end up in completely crashing a website for periods of time. None seem to be immune to DDoS attacks and this is considered as one of the biggest threats to the security on the Internet. In 2019 the most targeted industries were the gaming and financial services industries, followed by the internet & telecom, education and media & entertainment.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Denial of service occurs when a target machine is flooded with malicious traffic, and Distributed Denial of Service works in the same way, except that the attack is amplified by enlisting other machines and computers in the attack. Most DDoS attacks will rely on botnets, that is, on numerous compromised devices. In 2018 Github reported one of the largest DDoS amplification attacks that peaked at 1.35Tbps via 126.9 million packets per second.
When it comes to measuring the DDoS attack they can be broadly divided into three types: volume-based attacks, protocol attacks and application-layer attacks. Volume-based ones, later explained as UDP floods, ICMP floods et cetera, work with the goal to saturate the bandwidth of the attacked site and the magnitude is measured in bits per second. Protocol attacks such as SYN flood, Ping of Death, Smurf and more, are fragmented packet attacks. This type of attack consumes actual server resources or those of firewalls and load balancers and it is measured in packets per second. Application layer attacks work with a goal to crash the web server and the magnitude is measured in requests per second.
Also, DDoS attacks can be connectionless or connection-based. A connectionless one does not require a session to be formally established before a sender/server can send data packets to a receiver/client. A connection-based one does.
Individually, there are many types of DDoS attacks which we will explain below:
1. Extortion / Ransomeware DDoS (RDDoS) Attacks
A ransom DDoS (RDDoS) attack is when malicious parties attempt to extort money from a company by threatening them with a distributed denial-of-service (DDoS) attack. The malicious actor may carry out a DDoS attack and then follow up with a ransom note demanding payment (typically in Bitcoin) to stop the attack, or they may send the ransom note threatening a DDoS attack first with details on how to pay the ransom and the threat of taking down the company’s digital services. In the second case, the attacker may not actually be capable of carrying out the attack, although it is not wise to assume that they are making an empty threat.
2. Nuke
Nuke attack sends corrupt and fragmented ICMP packets via a modified ping utility to the target, repeatedly sending the corrupt data to slow down the affected computer until it comes to a full stop. Eventually, the target machine goes offline or results in a crash or Blue Screen of Death in case of Windows. The most famous example of a Nuke attack was the 1997 WinNuke which exploited a vulnerability in Windows 95. Years later, a newer version of WinNuke surfaced that affected Windows NT, 2000 and XP, but it was quickly patched by Microsoft. Nuke is an old type of DDoS attack and almost no modern operating systems are vulnerable to such an attack.
3. Peer to Peer Attacks
In a peer-to-peer attack, there is no botnet and the attacker doesn’t have to communicate with the clients it subverts. Instead, the attacker acts as a “puppet master”, instructing clients of large peer-to-peer file sharing hubs to disconnect from their peer-to-peer network and to connect to the victim’s website instead. The frequency and magnitude of peer-to-peer enabled denial of service attacks are increasing. Most P2P networks are based on the DC++ client. Each client in a DC++ based network is listed in a network hub. It is this hub software that is at risk of compromise.
4. Permanent DOS Attacks
Also known as “phlashing”, a permanent DOS attack damages a system so badly that it requires replacement or reinstallation of hardware. It exploits security flaws that allow remote administration of routers or printers, or other networking hardware. The attacker will replace the device’s firmware with a corrupt firmware image which will subsequently “brick” the device, rendering it unusable for its original purpose until it can be repaired or replaced. PhlashDance is an example of such a tool that was created by Rich Smith and used in 2008 to detect and demonstrate PDoS vulnerabilities at the security conference in London.
5. Reflected or Spoofed Attack
A spoofed DDoS attack is a process in which one host (a router, or a server) sends a flood of network traffic to another host. The term “spoofed” simply means that the origin host lies to the target machine about its identity. This is what also makes blocking the attack very difficult. All “spoofed” packets contain headers with a different IP address or hostname. The target machine believes everything contained in the packet header and this results in confusion by the target as to where the flood of traffic came from. Many services can be exploited to act as reflectors, some harder to block than others.
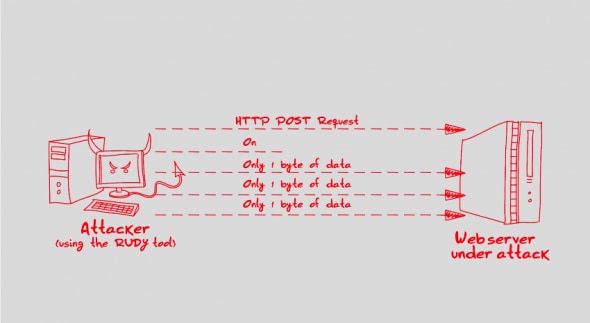
6. Rudy
RUDY also known as “Are you dead yet?” or “R-U-Dead-Yet?” targets web applications by starvation of available sessions on the web server. It is a popular low and slow attack tool that is designed to crash a web server by submitting long-form fields. The attack is executed via a DoS tool that browses the target website and detects embedded web forms. Once the forms have been identified, RUDY sends a legitimate HTTP POST request with an abnormally long content-length header field and then starts injecting the form with information, one byte-sized packet at a time. The information is sent in small chunks at a very slow rate, which explains “low and slow”. Ultimately, it is very effective because it will exhaust the targeted server’s connection table, causing the server to crash.
7. Slow Read Attack
Slow read attack sends legitimate application layer requests but reads responses very slowly, thus trying to exhaust the server’s connection pool. Basically what happens is that the client sends a full request, but when a server responds, it advertises a very small TCP window for accepting response data. Thus the server sends data slowly to the client keeping its sockets open. It keeps probing the client to check its receive windows size while the client always advertises a small window size, slowing down the transfer. The larger the file size, the more time it will take to complete such connections.
8. UDP Flood
User datagram protocol or UDP is a sessionless or connectionless networking protocol. It is ideal for traffic that doesn’t need to be checked and rechecked, such as chat or VoIP. But this also makes it vulnerable to UDP flood, a type of DoS attack in which the attacker overwhelms random ports on the targeted host with IP packets containing UDP diagrams. As more and more UDP packets are received and answered, the system becomes overwhelmed and unresponsive to other clients. The attacker may also spoof the IP address. If so, the return ICMP packets won’t reach their host and the attack will be anonymized. There are many commercially available software packages that can be used to perform a UDP flood attack, such as UDP Unicorn.
9. Smurf
A smurf attack relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address of the network, rather than a specific machine. Since a single Internet Broadcast Address can support a maximum of 255 hosts, a smurf attack amplifies a single ping 255 times. The attacker will send large number of IP packets with the source address faked, to appear to be the address of the victim. This can slow down the victim’s computer to the point where it becomes impossible to work on. In the late 1990s many IP networks would participate in Smurf attacks if prompted. Today, administrators can make a network immune to such abuse.
10. Ping of Death
In a POD type of attack, an attacker attempts to crash, destabilize or freeze the targeted computer or service by sending malformed or oversized packets while using a simple ping command. The ping command is usually used to test the availability of a network resource. It works by sending small data packets to the network resource. The ping of death takes advantage of this and sends data packets above the maximum limit, that is 65,536 bytes, that TCP/IP allows.
11. Teardrop
A teardrop attack is a denial of service attack conducted by targeting TCP/IP fragmentation reassembly codes. This attack causes fragmented packets to overlap one another on the host receipt. The host then attempts to reconstruct them during the process but fails. As a result, the data packets overlap and quickly overwhelm the victim’s servers causing them to fail.
12. SYN Flood
A “three-way handshake”, which is a reference to how TCP connections work, is the basis for this type of attack. Which basically reads as: a synchronize message or SYN is sent to the host machine to start the conversation. Then, the request is acknowledged by the server; it sends an ACK flag. Thirdly, the connection is completed when the requesting machine closes the connection. In a SYN flood attack repeated spoofed requests are sent from a variety of sources at the target server. The server will respond with an ACK packet but instead of closing the connection, the connection is allowed to timeout. Eventually, and with a strong enough attack, the host resources will be exhausted and the server will go offline.
13. ICMP (Ping) Flood
Similar in principle to the UDP flood attack, an ICMP flood overwhelms the target resource with ICMP Echo Request (ping) packets and sends packets as fast as possible without waiting for replies. The target server’s resources are quickly consumed, resulting in server unavailability.
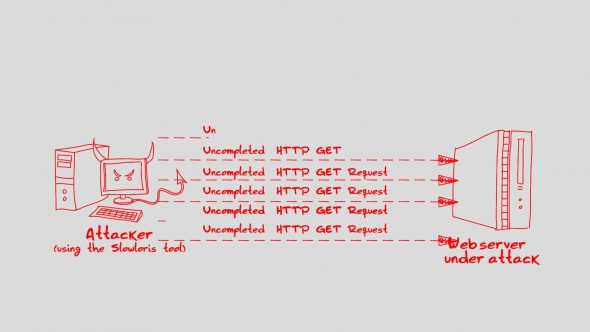
14. Slow Loris
Slow Loris is a DDoS attack software that enables a single computer to take down a web server. It was designed by Robert “RSnake” Hansen, a renowned security researcher. The attack requires minimal bandwidth to implement and affects the target server’s web server only, with almost no side effects on other services and ports. It works by opening multiple connections to the targeted web server and keeping them open as long as possible. It continuously sends partial HTTP requests, none of which are ever completed. Ultimately, the targeted server’s maximum connection pool is filled and additional connection attempts are denied. The most notable use of Slow Loris was in the 2009 Iranian presidential election.
15. Degradation of Service Attack
The goal of this attack is to slow down the response time of a website to a level that makes it unusable for most people. Zombie computers are leveraged in this case to flood the target machine with malicious traffic that will cause page performance and page loading issues. These types of attacks can be difficult to detect because the goal is not to take the website offline, but to degrade performance. They get to be confused with simply an increase in website traffic.
16. Multi-Vector
Towards the end, we have reached to describe the most complex type of DDoS attack: the multi-vector. In a multi-vector attack, a combination of different DDoS attack tools and approaches are merged together to put the target at a halt. It is usually aimed at a specific application on the target server or it is aimed to flood the target with a large volume of malicious traffic. It not only comes in different forms, but it targets different resources simultaneously, drags on for days, and it is extremely difficult to evade. In 2020, those businesses that suffered a DDoS attack saw their organization taken completely offline due to these forms of intrusions that strike the application layer and the network layer at the same time.
17. Zero-Day
A very popular term in the hacker community, zero-day simply symbolizes unknown or new attacks for which no patch has yet been released. They are also very difficult to protect against as they originate from an unknown threat. Despite the fact that the attacks are becoming more pervasive than ever before, it is still possible to mitigate them by utilizing a cloud-based DDoS protection service that offers a more holistic, proactive approach.
Attempts at bringing down websites and new types of DDoS attacks will continue to be an overgrowing threat to all-size businesses in the fore coming years. While various new insights are offered into new types of DDoS attacks that are ramping up, there is also a constant seeking out of vulnerabilities to compromise the site server, by the violators. The more complex the intrusions get, the more sophisticated solution is advised. Think of nothing less than proactive monitoring to prevent DDoS attacks from ever reaching your organization because by then it could be too late and you could suffer serious harm. Remember, money never sleeps.
Learn more about anti-DDoS solutions, or talk to our engineers to find your ideal solution.






