There’s been a lot going on recently in the DDoS mitigation field with two of the biggest DDoS (1.3 Tbps attack and 1.7 Tbps attack) attacks that ever happened all happening at the same time – with only four days apart from each other.
Previously the Mirai botnet and the exploitation of IoT devices has spawned the infamous Dyn attack that ‘brought down half the internet in 2016’, making it the biggest recorded attack at the time. This time the type of attack is a reflection amplification DDoS attack that uses memcached servers to amplify attacks by a factor of 10,000 to 51,000. This type of attack doesn’t even need a botnet to be potentially more powerful than the Mirai attack.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

We wanted to touch base and explain what are the actual repercussions of these attacks, how they were launched and explain all the details behind the launch.

The DDoS Attack Anatomy
To start things off let’s first dive into how a reflection amplification DDoS attack works.
Reflection amplification attacks have always been one of the strongest weapons for malicious actors, allowing them to amplify the power of their botnets (a group of infected computers controlled as a group) that are sending requests by staggering factors while also hiding the source of their attack behind a server they used to amplify the launched attack. The simple capability of turning small requests into larger while also not being seen as the attacker has changed the DDoS landscape drastically.
A good example of a reflection amplification attack (other than the ones we’ll mention below) is a DNS amplification attack.
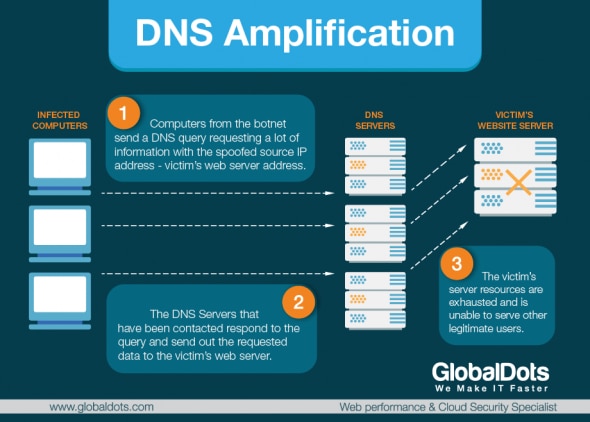
DNS reflection amplification attacks are asymmetrical DDoS attacks in which the attacker sends out a small look-up query with spoofed target IP (using the UDP protocol), making the spoofed target the recipient of much larger DNS responses (also using UDP protocol). With these attacks, the attacker’s goal is to saturate the network by continuously exhausting bandwidth capacity. Vulnerabilities in DNS servers are exploited to turn initially very small queries into much larger payloads. This, in turn, brings the victim’s servers down.
The reflection is achieved by eliciting a response from a DNS resolver to a spoofed IP address. During the attack, the perpetrator sends a DNS query with a forged IP address to an open DNS resolver, prompting it to reply back to that address with a DNS response. Because numerous forged queries are being sent out, and because DNS resolvers reply simultaneously, the victim’s network is overwhelmed.
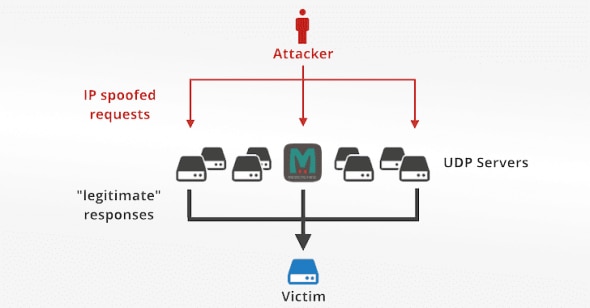
The above is what an attack using a DNS server to amplify attacks looks like. Now let’s see how a reflection amplification attack that is using Memcached servers looks like.
What is Memecached and who is using it
Memcached (pronounced “mem-cash-dee”) is an open source software that many organizations instal on their Linux servers to cache data and ease the workload on heavier data stores (disk or databases). It works by caching data in system memory and is intended for use only behind a firewall and on enterprise LANs – and this is where the problem begins.
A lot of organizations have hosted Memcached in such a way that it is easily approachable from the public internet even though it is highly recommended practice not to do so since it communicates using UDP (port 11211) which allows communication without any authentication. Now, all that attackers have to do is to search for these hosts, send a spoofed IP address of the intended victim, and then use them to direct high-volume DDoS traffic. From various sources it has been reported that currently there are 50,000 Memcached servers available for exploit on the public internet.
The geographical distribution of Memcached servers that can be abused (taken from Shadowserver.org):

The true power of a DDoS attack that is using a Memcached server lies in the fact that a Memcached server amplifies the original request by a factor of up to 51,200. This is more than a hundred times larger than the amplification factor DNS servers have as reflectors in an reflection amplification attack.
“With DNS amplification, for instance, an attacker might be able to generate a 50KB response to a 1KB request. But with a Memcached server, an attacker would be able to send a 100-byte request and get a 100MB or even 500MB response in return. In theory, at least, the amplification could be unlimited”
– Karsten Desler (CTO of Link11)
This is possible due to the fact that attackers are able to influence the amplification factor of Memcached servers for any given nodes by inserting records into the open server while also maliciously configuring the constraint on the size of the said records. This allows them to use larger objects when using Memcached servers as reflectors and reach amplification factors of never-before-seen sizes.
There’s more – ransom notes!
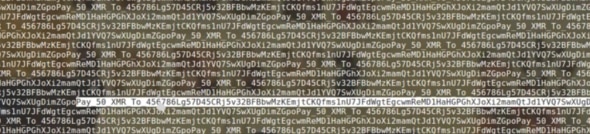
As reported by KrebsOnSecurity in a detailed article, there have been reports that attackers are adding short ransom notes and a payment address into the junk traffic they’re sending to Memcached services. Since Memcached can accept files and host them in its temporary memory, the attackers place a 1 mb file full of ransom requests onto the server and request that file thousands of times to be sent to the victims IP address.
An example of a ransom note requesting 50 XMR (Monero virtual currency):
The interesting thing about running DDoS attacks using Memcached servers is that it has always been possible – attackers just haven’t considered this option until now, and now they’re using it intensely which can be seen here, where’s there’s a live running list of the latest targets that are getting attacked.
How to stop the attacks
There’s been a worldwide debate on how to best approach this problem and stop this type of attacks running once an for all. The first suggestion to anyone running a server which has Memcached installed is to block the 11211 port to prevent hackers from accessing it.
However, it’s a bit much to expect every system admin in the world will be able to react in time – and this is why every website needs to be prepared for an attack of this magnitude.
Luckily, GlobalDots can help you protect your business from DDoS attacks of any size and intensity. Even with the most complex and sophisticated setups, GlobalDots can provide you with the technology stack that ensures that the most important aspects of your site are always up & running: deliverability, speed, availability, failover and web security (including web application protection, bot protection, DDoS protection and mitigation).
Customers like Lufthansa, Playtika, Trading View, Lamborghini, Bosch, Fiat, Rocket Internet, Benetton, Bulova and other leading brands and small-medium enterprises rely on GlobalDots services to keep their sites and applications fast & secure. Contact us today to help you out with your performance and security needs.






