Providing employees with secure access to enterprise applications deployed behind the firewall is a core requirement for all businesses. Enterprises must also deal with the riskier proposition of providing access to a varied list of contractors, suppliers, partners, customers, and developers.
Regardless of where these applications are hosted—whether in a public cloud or private data center—this is a complex, cumbersome task requiring on-premise hardware and software such as application delivery controllers (ADC), virtual private networks (VPN), identity and access management (IAM) systems, and more.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Yet with all of these technologies, enterprises are still exposed to a variety of security risks stemming from the fact that access to internal applications opens up the entire network to attack.
To counter these challenges, enterprises have started to rely on zero trust security. In this article we’ll discuss zero trust security implementation.
What is Zero Trust Security?
Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter. No single specific technology is associated with zero trust; it is a holistic approach to network security that incorporates several different principles and technologies.
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.”
Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.
- A zero trust network is built upon five fundamental elements:
- The network is always assumed to be hostile
- External and internal threats exist on the network at all times
- Network locality is not sufficient for deciding trust in a network
- Every device, user, and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
Zero Trust leverages tools like security information management, advanced security analytics platforms, security user behavior analytics, and other analytics systems to help security experts observe in real-time what is happening within their networks so they can orient defenses more intelligently. The focus on the analysis of cyber-related event data can help develop proactive security measures before an actual incident occurs.
The bottom line is data authentication is the foundation of Zero Trust. Users, endpoints, email and cloud applications have become communication channels that serve as attack vectors. In a Zero Trust model where you cannot trust anyone or any device, focusing the perimeter around data protection with intelligent authentication is the best security approach. Therefore, agencies must have a clear understanding of their users and their roles, their data, and their technology assets before beginning to implement Zero Trust.
Zero Trust is not dependent on a location. Users, devices and application workloads are now everywhere, so you cannot enforce Zero Trust in one location – it must be proliferated across your entire environment. The right users need to have access to the right applications and data.
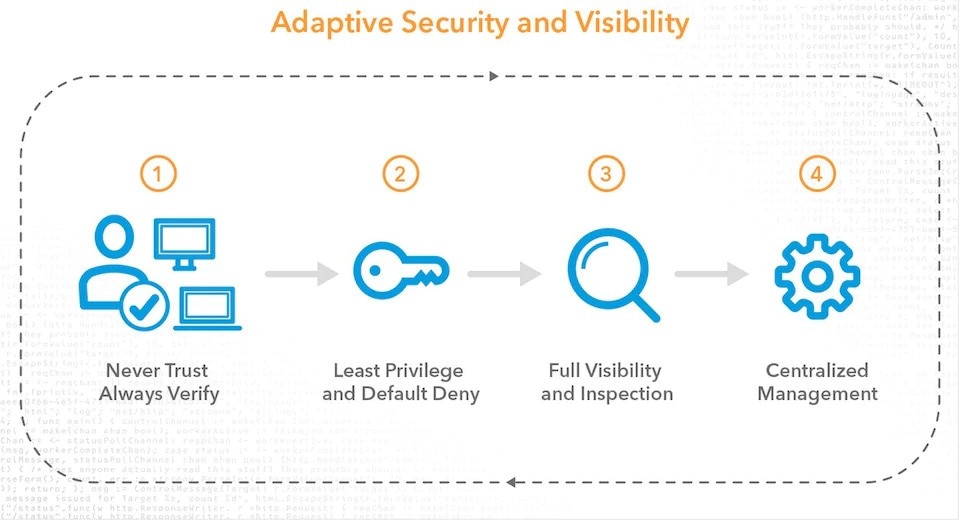
Zero Trust Implementation
Here are the steps for implementing a zero trust access architecture.
Utilize Microsegmentation
Zero trust networks also utilize microsegmentation. Microsegmentation is the practice of breaking up security perimeters into small zones to maintain separate access for separate parts of the network. For example, a network with files living in a single data center that utilizes microsegmentation may contain dozens of separate, secure zones.
A person or program with access to one of those zones will not be able to access any of the other zones without separate authorization.
Use Multi-Factor Authentication (MFA)
MFA is the basic building block of an intelligent approach to network security. Properly used, it reflects the guiding principle of zero trust: “never trust, always verify and verify again.”
MFA requires the presentation of two or more authentication factors: a knowledge factor (something only the user knows such as a password, PIN, or a pattern), a possession factor (something only the user has such as an ATM card, smart card, or mobile phone), and an inherence factor (something which contains a biometric characteristic such as a fingerprint, retina scan or face scan). Upon presentation, each factor must be validated for authentication to occur.
Implement Principle of Least Privilege (PoLP)
The principle of least privilege (POLP) is the practice of limiting access rights for users to the bare minimum permissions they need to perform their work. Under POLP, users are granted permission to read, write or execute only the files or resources they need to do their jobs: In other words, the least amount of privilege necessary.
Additionally, the principle of least privilege can be applied to restricting access rights for applications, systems, processes and devices to only those permissions required to perform authorized activities.
Validate all endpoint devices
Just like users, devices cannot be trusted without verification. To achieve Zero Trust Security, identity-centric controls must be extended to the endpoint. That means every device used to gain access to corporate resources must first be enrolled so that it can be recognized and verified.
Device verification should enable an organization to determine whether the endpoint seeking to access internal resources meets its security requirements.
Conclusion
By implementing zero trust security, enterprises improve control over who has access to what resources. This also reduces an organization’s attack surface and prevents lateral attacks by making unauthorized resources unreachable or even invisible. Also, zero trust security enables greater visibility through activity monitoring.
If you have any questions about how we can help you establish a zero trust architecture, contact us today to help you out with your performance and security needs.






