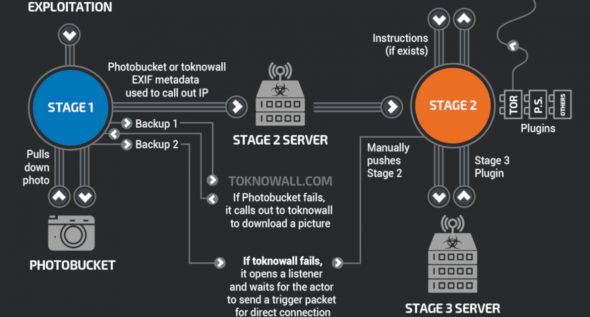
Security researchers from Cisco’s Talos cyber intelligence have today uncovered more details about VPNFilter malware, an advanced piece of IoT botnet malware that infected more than 500,000 routers in at least 54 countries, allowing attackers to spy on users, as well as conduct destructive cyber operations.
Initially, it was believed that the malware targets routers and network-attached storage from Linksys, MikroTik, NETGEAR, and TP-Link, but a more in-depth analysis conducted by researchers reveals that the VPNFilter also hacks devices manufactured by ASUS, D-Link, Huawei, Ubiquiti, QNAP, UPVEL, and ZTE.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

To hijack devices manufactured by above listed affected vendors, the malware simply relies on publicly-known vulnerabilities or use default credentials, instead of exploiting zero-day vulnerabilities.
Besides this, the researchers primarily shared technical details on a new stage 3 module, named “ssler,” which is an advanced network packet sniffer that, if installed, allows hackers to intercept network traffic passing through an infected router and deliver malicious payloads using man-in-the-middle attacks.
This 3rd-stage module also makes the malware capable of maintaining a persistent presence on an infected device, even after a reboot.
Read more: The Hacker News






