High volume, low margin means domination for giants like Akamai
Right now, as Bizety clearly states, Akamai has the biggest market opportunity ever in the DDoS Mitigation service industry. Reason for this is that DDoS mitigation is splitting up into two market segments – one segment being protection from large scale DDoS attacks and the other one being protection from intelligent DDoS attacks targeting the application layer. In the first segment there is currently only one company that can handle a multi-Tbps DDoS attack, and that is Akamai. In 6-12 months companies like Level 3, Verizon, Google, Azure and AWS will start to be able to compete in this market segment.

Read more: Bizety
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

A/B testing at the edge
Fastly published an interesting post about A/B testing at the edge and how exactly do they do it. A/B testing means sending traffic to two different variants of the same page and seeing which one works better in favor of your objective or business goal. What Fastly does is they A/B test at the edge, which means closer to their users. This enables users to not suffer decreased performance while a seperate segmentation service is consulted, and also prevents delays on the client while it re-renders the page.
A/B testing can be as simple or as complicated as you want it to be. You can build elaborate multivariate test frameworks, or use a variety of commercial tools to set up tests either serverside or clientside. Sometimes, you just want to run a quick check to validate that a change didn’t make anything worse — perhaps a lack of change is exactly what you are looking for. Either way, you won’t know for sure until you look.
Read more: Fastly
Dyn outage analysis by Cloudflare
Dyn has issued an official statement about the outage of their DNS service which we’ve mentioned in the previous week, but now, all over the internet we are seeing detailed reports of what actually happened in great detail. One of the best coverage is done by Cloudflare on their blog. Cloudflare, as you may know, has customers that also use Dyn Managed DNS and they’ve explained why these customers experienced lower traffic. Long story short, in the second case below where the origin is configured with a CNAME, Cloudflare needs to perform an external DNS lookup to resolve the target of the CNAME to IP addresses. In many cases the target of a CNAME is handled by a third party DNS provider and if the DNS provider (Dyn in this case) is unable to answer the query, Cloudflare is unable to resolve the domain to an origin IP and cannot serve the request.
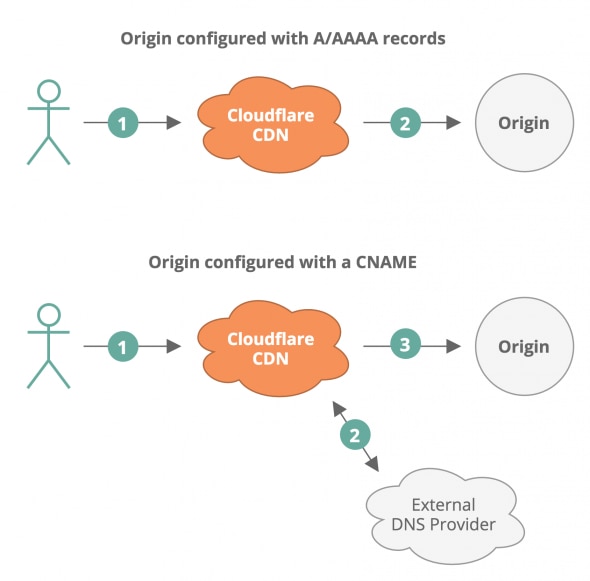
Read more: Cloudflare
Takeaways from the Dyn outage
The latest DDoS attacks on Dyn and Brian Krebs are a defining moment for the CDN industry because up until last year, content delivery companies weren’t concerned with large-scale DDoS attacks. We’ve already stated that Akamai is the only mitigation provider right now who can handle 1Tbps attacks, but 2Tbps attacks are just around the corner! Here are some takeaways:
- Dyn has two choices: Partner up with Akamai or build massive capacity
- Large content companies will employ a multi-DNS provider strategy, possibly building some internal capabilities
- Expect that IoT DDoS attacks will become the new norm and start happening on a weekly basis
- The DDoS Mitigation business will become a high volume, low-profit business similar to video streaming which means DDoS Mitigation PoPs will cost around $2M per year
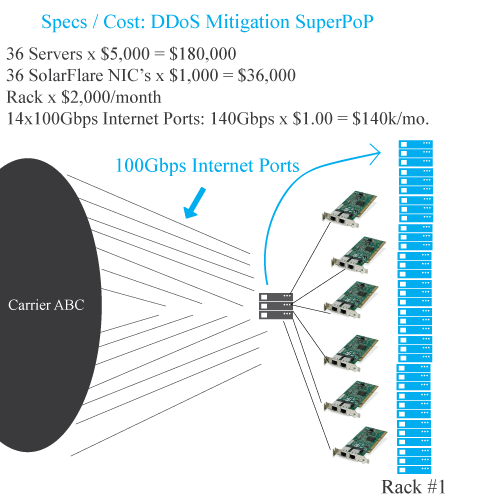
Read more: Bizety
Financial services too?
Akamai stated that the Dyn outage also had impact across the financial services industry – banks, insurance companies and others. Here’s a short preview for US banks, and if you want to read more about specifics, follow the link below.
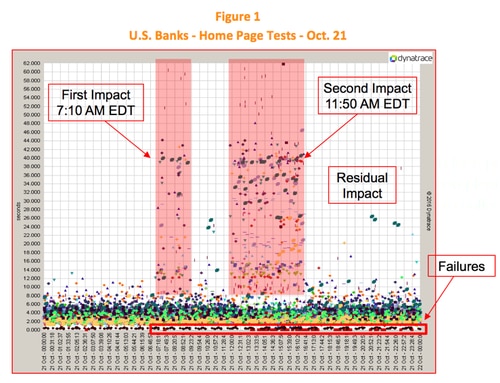
Observations:
1. The first impact is shown beginning at 7:10 AM EDT, with a drastic increase in page response times for a number banking home pages. This 7:10 mark matches the attack time of 11:10 UTC reported by Dyn.
2. The second major impact started at 11:50 AM EDT. This also matches the time of the second attack reported by Dyn.
3. There was residual impact late into the evening for a number of banks, again matching Dyn reports.
4. Some banks had complete failures of their home pages during this period.
5. Close examination shows that 28 of the 42 banks (2 out of 3) had impact due to this event on Oct. 21. (Please don’t draw the conclusion that “two-thirds of the banks in the U.S. were impacted by the attack”. We are only looking at 42 of the more than 6,000 banks on the FDIC list of banks in the U.S.)
Read more: Akamai






