120,000 Sites Affected by Cloudflare Data Leak
A severe security flaw in Cloudflare’s systems was disclosed last week. Apparently, it leaked customer data, live samples, encryption keys, cookies, passwords, POST data chunks and even HTTPS requests due to a Heartlbleed-like bug.
The system flaw was discovered by Tavis Ormandy, Google’s Project Zero researcher and bug-bounty hunter. Ormandy proceeded to privately inform Cloudflare about the security issue followed by an announcement on Twitter.
Cloudflare CTO John Graham-Cumming informed that the vulnerability has since addressed, although sensitive user data was exposed. The leak affected a number of web-based services such as Uber, Fitbit and OK Cupid among thousands of others. The company stated the leak was rooted in three “minor” features which had since been deactivated. According to Graham-Cumming, the first of them was activated on September 22, reached highest potential impact on February 13, and lasted until Ormandy’s disclosure on February 18.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

The issue was dubbed Cloudbleed as it showed similarities to Heartbleed, a major OpenSSL vulnerability disclosed in 2014 which also leaked sensitive data.

Read more: Hacking Threat, Cloud Pro
Chinese IT Company to Acquire CDNetworks
According to numerous reports last week, ChinaNetCenter, a Chinese Internet service platform provider is likely to acquire CDNetworks, South Korean full-service content delivery network. CDNetworks was established in 2000 and is the largest regional and third largest global provider of CDN services in the market.
With around 1 300 clients like Samsung, Hyundai and Ebay, across 98 countries, the CDN powerhouse was acquired in 2011 by KDDI Co., a Japanese telecommunications operator. In 2015 CDNetworks reported EBITDA reached $7.68 billion. On the other hand, ChinaNetCenter is a key player in the Chinese CDN market, holding a 40.6 % share of the landscape as of 2015.
ChinaNetCenter announced they are looking to purchase a 97.83% stake in CDNetworks for a total of $187 mil. A ChinaNetCenter official stated that this acquisition will hopefully help their efforts of advancing into the global market.
Read more: Pulse News
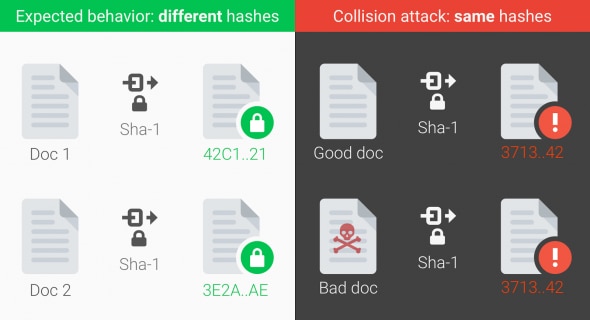
Researchers Discover SHAttered – The SHA-1 Collision Attack
The 22-year old cryptographic hash function SHA-1 is counting its last days of glory. Researchers from the CWI Institute in Amsterdam partnered with Google Research concluded a two year long process aimed to discover an accelerated way to compromise the SHA-1 function.
Dubbed ‘SHAttered’, the newly disclosed attack vector will further push the vulnerable algorithm towards its last days. The researchers studied the collision of two PDF files and found that a SHA-1 collision attack enables the mimicking of a digital signature of one PDF file to be used as signature for a second PDF. This type of collision refers to generating the same hash numerous times, which means a hacker could trick the system into accepting malicious content in place of legitimate one. Practically, attackers could easily replace files without ever being detected.
The research team announced that in order to discover the new vulnerabilities and test the attack they had to run a total of nine quintillion SHA-1 computations, which required 6 500 years of CPU computation time to complete phase one and nearly 110 years of GPU computations to complete phase two.
In line with Google’s policies for vulnerability disclosures, researchers will wait 90 days before releasing the proof-of-concept for the collision attack. In the meantime, a protection that detects the PDF collision method was added to Gmail and GSuite users as well as a public and free detection system.
Read more: Hacking Threat, Google Blog
SaaS and IaaS Will Lead Cloud Growth Until 2020
According to both Gartner and IDC 2017 cloud predictions, this year will find a strong growth which is slowly going to slow down over the next few years.
“The global public cloud market is entering a period of stabilisation, with its growth rate peaking at 18% in 2017 and then tapering off over the next few years”
Gartner research director, Sid Nag
Numbers from the IDC report predict cloud growth will slow to 21.5% in 2020, down from 24.4% expected this year. Both companies agree that organisations are currently merely tapping the baseline potential of the cloud, which is expected to change over the next three years. They predict enterprises will start using more advanced applications, propelling cloud usage to the next level.
The reports estimated that 50% of new 2017 large-enterprise application adoptions in North America will be composed of SaaS or other forms of cloud-based solutions. “The cloud will become more distributed, trusted, intelligent, more industry and workload specialised, and more channel mediated. As the cloud evolves new capabilities cloud use cases will dramatically expand.” This further evolution of the cloud is referred to as “Cloud 2.0” by IDC.
According to predictions, the two areas that will achieve highest levels of growth until 2020 will be IaaS and PaaS. Gartner predicts IaaS will grow 36.8% YoY, to a total 106% increase until 2020. IDC estimated CAGR of 30.1%, with similar annual growth levels in the next three years.
Read more: Cloud Pro
Dropbox Launches Slack Integrated SecurityBot
Looking to better protect enterprise data, Dropbox has launched an open source security bot that integrates with Slack. SecurityBot was developed to comb through Dropbox and detect unusual activities. When it track something suspicious, it proceeds to contact employees through Slack’s messaging platform to confirm if they were the ones to perform the action.
Depending on whether or not it thinks employees participated in the malicious incident, the information will then be forwarded to the security team.
Dropbox already tested the bot within the company and found the amount of time spent on worker review and outreach was reduced by 15%.
“It helps us greatly reduce the rate of false positives that have to involve the security team, and rather than spending their time repeatedly reaching out, our security engineers now have more time to focus on other projects and focus on improving our overall infrastructure security posture.”
Luke Faraone from Dropbox’s Infrastructure team
This extra layer of malicious activity detection will greatly help security teams which will no longer be swamped with possible threats, instead they will only be contacted when an incident requires to be addressed.
Read more: Cloud Pro






