Concerns over cloud security are obviously among top priorities for anyone involved in cloud business or managing the migration of their applications to the cloud. The trend continued to rise dramatically after the NSA incident (the leaking of classified documents detailing the data collection activities of the U.S. National Security Agency) and the users became more concerned over who to trust their data with – they are more careful, but they are not necessarily abstaining from the cloud. The issues of critical information infrastructure, legal issues, cryptography, certification and compliance are questioned in more depth, over and over again.
7 in 10 companies will still move apps to the Cloud
Nonetheless, the experts say that the future of cloud looks bright, 7 in 10 companies using cloud services will move new apps to the cloud, even though security in the cloud is a concern (source: Internap).
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Furthermore, according to a LinkedIn survey of 7,052 respondents, 54% said security is their top concern for transitioning to the cloud and indeed, security threats are many: application attack, brute force, malware/botnet, misconfiguration, web app attack…
However, if we consider the difference between the security of on-premise infrastructure and cloud service provider infrastructure, the numbers show that in most cases it is safer to trust your data with a service provider. In other cases, numbers do not vary that much (see comparison below).
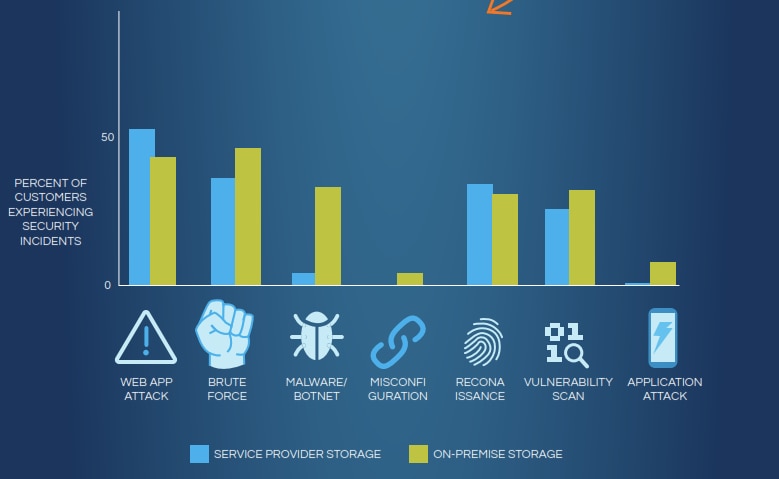
Source
At Internap, they suggest that you need to know more about your service provider, to be sure and they give example questions you should ask before trusting your data with the cloud:
- Are there exception monitoring systems available?
- How is staff access controlled?
- What are the data protection laws (in that specific area)?
- Can I obtain a security audit of your host?
- What third-party companies do you work with and will they be able to access my data?
- How are passwords created, protected and changed?
- Are guarantees and penalties available?
- Can you accommodate my existing security policies?
These questions should help you find out whether you’ll be working with a secure vendor or not, the most important of which probably being about the third parties involved in the business with the vendor.
Considering performance, infrastructure security and governance is crucial to successfully migrate applications to the cloud.
Predictions: Data Privacy will become a hot topic in 2014
Larry Warnock, president and CEO at Gazzang, reflected (for CloudTweaks) on recent NSA spying revelations and cloud security concerns, and predicted what this may mean for future innovative technologies:
- SaaS vendors will offer encryption keys revocable by end users
- Vulnerability of APIs will be exposed
- European companies migrate data from US-based cloud and SaaS providers in response to NSA Prism scandal. US-based cloud service providers including Google, Amazon and Microsoft account for approximately 85% of global markets. However, a recent Cloud Security Alliance survey of 500 respondents found that 56%of non-US residents were less likely to use US-based cloud providers in light of recent revelations about government access to customer information. In response, the EU’s European Cloud Partnership is drafting a charter to promote an EU-based digital cloud service
- As NSA concerns fade, data privacy concerns skyrocket. Most people and organizations will realize they’re not being targeted by the NSA; however, the residual effect of the spying scandal is that data privacy will become a scorching hot topic in 2014
- Major trustees of consumer data, such as Google, Yahoo and Facebook begin to offer consumer-based key management services, where the provider hosts the encryption and the end-user manages the keys to their personal data. Consumer cloud storage providers tend to design systems that emphasize recoverability over security
TwinStrata founder and CEO Nicos Vekiarides, predicts boldly (as reported by e-week) that the “encryption provided by cloud providers will be deemed insufficient because customers won’t own the encryption keys. Overall,” he claims, “2014 will be the year organizations become more aware of, and look to address exposure points along the data-supply chain.”
The predictions about NSA leaks causing loss in revenue for cloud providers in billions of dollars, proved untrue. But the impact on increased emphasis on cloud data security and protection that is only expected to grow in 2014, can not be neglected. Google and Microsoft both promised to have their data encrypted in the cloud. Dropbox announced similar data encryption programs… However, users will try and retain more control over their data. Many new cloud tools are being developed that support exactly this idea of businesses taking fairer advantage and control of cloud hosted infrastructure and services. Many cloud vendors will begin releasing transparency reports. Migration to the cloud will not face a slow down, but only a few further check-points on a speedy highway.
Feel free to address your concerns and predictions in the comments!







