APIs are no longer an edge case. In 2025, they’re a core requirement for maintaining trust, compliance, and operational continuity. As organizations build more API-driven systems—from customer apps to internal microservices—the exposure risk compounds. And quickly, too.
Even mature security teams are finding that traditional tools can’t keep pace with the volume, velocity, and nuance of modern API attacks.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Why API Security is a Priority in 2025
APIs have become the top attack vector in modern software. They’re everywhere across mobile, web, IoT, and backend systems. They’re often deployed fast with limited oversight. This combination of ubiquity and inconsistency creates a perfect storm for attackers.
Nearly half of organizations now say API security is a C-level topic, and 95% of CISOs rank it as a top priority for the next two years. The shift is driven by both the volume and sophistication of recent attacks:
- Duolingo exposed data on 2.6 million users via an unsecured API endpoint. It wasn’t a breach in the traditional sense. Instead, it was a scrape of poorly protected public data, including names, emails, and progress logs.
- T-Mobile has suffered six breaches in four years. The latest affected 76 million users and led to a $31.5 million settlement after attackers accessed personal details including Social Security numbers through misused APIs.
- In Australia, Optus lost data on 10 million customers—including passports and license numbers—after a long-forgotten API endpoint was left exposed. No sophisticated tools were involved in the attack, only persistence.
These aren’t isolated or novel. They’re systemic.
They represent a shift in attacker behavior. Today’s threats abuse legitimate API functionality through subtle misconfigurations and logic gaps. They unfold slowly and blend in with normal traffic, easily bypassing perimeter tools.
APIs are also changing constantly. In many companies, 37% of APIs are updated on a weekly basis. Without continuous discovery and governance, shadow and zombie endpoints proliferate. If you don’t know what’s exposed, you can’t secure it.
What is API Security?
API security is the discipline of protecting Application Programming Interfaces (APIs) from misuse, abuse, and exploitation. While firewalls and secure coding can defend a static web app, APIs require protection at a much more granular level, because they expose not just data, but application logic.
According to OWASP, API security focuses on “strategies and solutions to understand and mitigate the unique vulnerabilities and security risks of APIs.” These include broken authentication, excessive data exposure, and logic abuse.
APIs often bypass UI layers and expose core system functions directly to consumers, mobile apps, and partners, requiring equal or stronger controls than the rest of your infrastructure.
How API Security Differs from Web Security
It’s a mistake to treat API security as an extension of web security. The architectural differences are substantial:
- More attack surface: A typical web app exposes one or two entry points. A modern API-first app exposes dozens or hundreds, often changing weekly.
- Non-browser clients: Web application firewalls (WAFs) were designed to inspect browser-based traffic. API clients include IoT devices, mobile apps, automated scripts, and third-party services. Traditional WAF rules often fail to capture or block these flows.
- Legit-looking attacks: Instead of blunt-force techniques like SQLi, attackers now mimic valid users, exploiting subtle logic flaws. These “low-and-slow” attacks are invisible to rule-based tools.
- Continuous evolution: In DevOps environments, APIs are pushed to production rapidly and often without deep review. Inventory becomes outdated fast, leaving shadow or zombie APIs unsecured.
This is why APIs are known as the new “front door” of enterprise risk and why pre-prod testing alone is no longer enough. Effective protection requires continuous, runtime awareness and policy enforcement.
The Modern API Threat Landscape
APIs are now the #1 attack vector for cloud-native applications. What’s changed isn’t just the volume of APIs; it’s the sophistication of attacks and the brittleness of defenses.
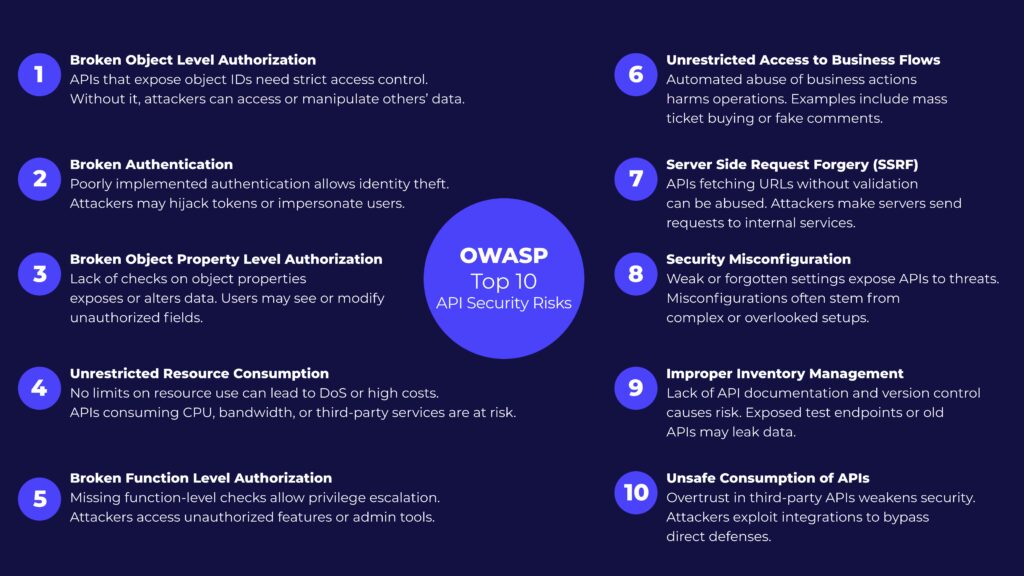
The updated OWASP API Top 10 highlights the most exploited weaknesses. Among them:
- Broken Object Level Authorization (BOLA): Still the top threat, responsible for ~40% of API breaches. Attackers manipulate object IDs to access other users’ data. Seen in high-profile incidents at USPS, Coinbase, and Peloton.
- Broken user authentication: APIs often have weak or missing auth. T-Mobile’s breach of 76 million records stemmed from this exact issue.
- Unrestricted resource consumption: Without rate limits, APIs can be overwhelmed, driving up cloud costs or enabling brute-force attempts.
- Improper inventory management: Many orgs lack a real-time API inventory, leaving deprecated or undocumented (zombie) APIs exposed. This is part of the DevOps-related misconfiguration we discuss below, and it was a core issue in the Optus breach, which affected 10 million Australians.
Also worth noting: the 2023 update added business logic abuse to the list. These attacks exploit legitimate API functionality—like checkout flows or search endpoints—in ways developers never intended.
DevOps-Related Misconfigurations
Modern CI/CD pipelines push updates constantly. Many companies update APIs weekly, without always tracking what’s deployed. Without auto-discovery, security teams fall behind.
Common issues include:
- Misconfigured access controls in CI/CD or infrastructure-as-code
- Leaked secrets via GitHub or CI pipelines
- Inconsistent enforcement of auth and logging
When API security isn’t centralized, oversight breaks down.
API Keys, Authentication Gaps, and Data Leakage
API keys are still widely used for authentication, but they’re often hardcoded, over-permissioned, and rarely rotated. Many breaches begin with a leaked key that grants full access to sensitive resources.
Authentication is frequently missing, broken, or misconfigured. In some cases, APIs are deployed publicly without any protection. In others, weak token schemes are reused or replayed.
APIs also tend to return too much data. Even if UIs filter it, the backend might expose full objects or verbose error messages. If the data’s there, attackers will find it.
How to Assess Your API Security Posture
A solid API security program starts with visibility and ends with continuous enforcement. Here’s how to assess your posture:
1. Inventory & Classification
Before you can protect APIs, you need to find them all. That includes:
- Internal and external APIs
- Deprecated or undocumented endpoints (zombie APIs)
- Third-party integrations and partner-facing APIs
Automated discovery tools are essential here. They give you visibility into endpoints, request methods, parameters, and associated data types. Once identified, classify APIs by:
- Business criticality
- Data sensitivity (e.g., PII, payment info)
- Exposure level (public, internal, partner)
This helps prioritize where to apply controls and which APIs deserve deeper testing.
2. Threat Modeling
With inventory in place, threat modeling highlights how those APIs might be abused. The goal isn’t just to find technical vulnerabilities but also to understand how an attacker would chain legitimate requests to do damage.
Model for:
- Broken object or function-level access (BOLA, BFLA)
- Abuse of business flows (e.g., ticket scalping, scraping, rate abuse)
- Data leakage and over-permissioning
- Misuse of public or third-party integrations
Integrate threat modeling into your API design process, especially for high-risk or external-facing APIs.
3. Testing: Static, Dynamic, and Fuzzing
A layered testing strategy exposes vulnerabilities at multiple levels:
- Static Application Security Testing (SAST): Scans source code before deployment. Useful for catching OWASP Top 10 issues, hardcoded secrets, and insecure function usage.
- Dynamic Application Security Testing (DAST): Runs attacks against a live app to test actual behavior. Useful for misconfigurations, input validation, and business logic flaws.
- API Fuzz Testing: Sends malformed or unexpected inputs to probe how the API handles edge cases, crashes, or leaks. Effective for unearthing unknown risks in serialization, parsing, and error handling.
Combine automated scanning with periodic manual penetration testing, especially for public APIs and critical integrations.
4. Continuous Monitoring
Security doesn’t stop at deployment. You need real-time visibility into how APIs behave under load, across geographies, and over time.
Log and analyze:
- Request patterns and rate anomalies
- Unauthorized access attempts
- Misuse of credentials or tokens
- Behavior that deviates from documented API usage
Use logs enriched with user IDs, IPs, and timestamps to support incident response and threat hunting. Look for signs of API drift, where deployed behavior deviates from spec or intended logic.
AI & Behavior-Based Detection for API Protection
Modern API abuse often looks like normal traffic. That’s where behavior-based detection and AI come in.
AI-powered tools establish a baseline for what normal API use looks like. Then they flag deviations, like unusual request timing, geo-location anomalies, or behavioral inconsistencies.
Real-Time Threat Detection That Understands Context
Modern AI security platforms analyze vast amounts of API telemetry (user IDs, request paths, methods, frequency, and payload size) to establish a baseline of normal behavior. Once that baseline is established, any anomaly becomes a signal.
Unlike rule-based engines, these systems:
- Detect low-and-slow reconnaissance that unfolds over days or weeks
- Identify automated scraping, credential stuffing, and abuse that mimic user behavior
- Recognize API drift
- Flag zero-day activity that doesn’t rely on known exploits or traffic spikes
False positives go down. Detection time improves. And response windows shrink from hours to seconds.
In our own analysis, Senior Engineer Ganesh describes how the rise of API-driven applications has created a massive, moving target for attackers. Most developers, focused on functionality, don’t model threats the way attackers do. That gap is where AI shines.
Here’s what AI protection looks like in action:
- Continuous discovery of all APIs (whether public, private, or partner-facing) across changing cloud environments.
- Real-time risk scoring based on behavioral patterns, not static threat feeds.
- Zero-day defense that detects attacker reconnaissance at the source layer, before a payload is ever launched.
- Developer-centric insights that connect anomalous activity back to vulnerable API functions and recommend mitigation steps.
The advantage isn’t just speed. It’s adaptable. AI systems evolve with your stack, without requiring constant rule tuning or manual config.
In 2025, any serious API security strategy should include an AI-enhanced detection layer. Not as a nice-to-have, but as a critical defense against the kinds of threats legacy tools were never designed to see.
API Security for DevOps Teams
In API risk in DevOps, Miguel Fersen highlights a recurring issue: leaked cloud API keys. Whether through GitHub commits, misconfigured CI/CD pipelines, or careless backups, API access keys often find their way into public view, and bots are watching.
DevOps accelerates delivery, but without proper safeguards, it can also accelerate exposure. Security teams can’t just rely on post-deployment scans. Protection has to be integrated into every stage of the software delivery lifecycle.
Shift-Left Integration and CI/CD Tooling
“Shift left” means embedding security early, before code hits production. For APIs, this includes:
- Secrets scanning: Automate scans to detect hardcoded credentials (e.g., API keys, tokens) in commits and CI pipelines.
- Static analysis and SCA: Run security testing tools like SAST and Software Composition Analysis (SCA) during build stages.
- Peer code reviews: Include secure design and logic validation as part of review checklists.
- IaC scanning: Validate Kubernetes, Terraform, and other cloud-native configs for misconfigured roles, ports, or access controls.
These practices help catch issues before they ship, but they’re not enough on their own.
Runtime Controls and API Gateways
Once APIs are live, you need visibility and enforcement in production. Runtime defenses include:
- API gateways: Serve as a choke point for traffic enforcement, implementing rate limits, schema validation, IP filtering, and basic authentication.
- WAFs: Add another layer of traffic filtering, though they’re limited in understanding API-specific logic.
- Runtime Application Self-Protection (RASP): Monitors behavior from inside the app, enabling high-fidelity blocking of abnormal activity in real time.
But even these controls require proper configuration, and DevOps teams often skip them for speed. That’s where the real risk lies.
Real-world examples include:
- Tesla’s AWS keys exposed on GitHub, leading to crypto-mining abuse.
- A WordPress developer racking up $6,000 in AWS charges overnight after exposing wp-config.php.
- A startup founder whose API key was compromised within five minutes of uploading code to GitHub.
Assume credentials will leak. Design for containment. Apply the principle of least privilege, limit scopes, and monitor for unusual usage patterns.
DevOps isn’t the enemy. But speed without control creates risk. The best API security strategies balance agility with guardrails that don’t get bypassed under deadline pressure.
API Governance & Strategic Security Architecture
Good API security isn’t just about blocking traffic. It’s about how APIs are designed, authenticated, authorized, and retired (their architecture). Governance ensures APIs don’t become long-term liabilities.
Zero Trust for APIs
A Zero Trust approach means assuming every API is exposed, even if it’s internal. Instead of relying on perimeter controls, you enforce strict identity checks and behavioral validation at every point of interaction.
Key elements include:
- Authentication on every request
- Microsegmentation by role or workload
- Real-time behavioral analytics
Treat APIs like user identities: no default access, always verified, always observed.
Strong Auth & Fine-Grained Permissions
Broken authentication and misconfigured permissions are among the most common causes of API breaches. Fixing them requires:
- OAuth2 and JWTs for secure token-based authentication
- Token scoping and expiration to reduce exposure time
- RBAC and PoLP to limit access to only what’s required for a given operation or user.
- Multi-factor authentication for any high-privilege or sensitive functions
APIs should never rely on API keys alone. They’re too easily leaked, too hard to manage, and too often over-permissioned.
Versioning and Lifecycle Control
Without governance, APIs linger, and attackers know how to find them. APIs should evolve safely:
- Use versioning (v1, v2, etc.) and sunset deprecated endpoints
- Maintain a living inventory—no orphaned APIs
- Document with OpenAPI/Swagger and validate against runtime
- Enforce security reviews before deployment
Governance isn’t overhead. It’s the guardrail that keeps agility safe.
In a Nutshell: Security Must Scale with Speed
In 2025, APIs are the interface to everything: your data, your services, your customer experience. Securing them must be an architectural commitment.
The attackers aren’t slowing down. They’re evolving, automating, and targeting business logic at scale. But with the right assessment strategies, behavior-aware defenses, and governance principles in place, your team can stay ahead.
Security doesn’t scale by accident. It scales by design
Don’t wait for an incident to trigger your API security strategy. Book a free API Security Assessment with GlobalDots.






