Enterprises are moving to cloud-based environments at an ever-increasing pace. Cloud infrastructure offers many benefits, and it enables organizations different options and possible set-ups (public cloud, hybrid cloud etc.).
However, security remains a top concern among enterprises which are moving to cloud-based infrastructure. Cloud computing continues to transform the way organizations use, store, and share data, applications, and workloads. It has also introduced a host of new security threats and challenges. With so much data going into the cloud—and into public cloud services in particular—these resources become natural targets for bad actors.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

While using cloud technology offers many advantages compared to on-prem models (scalability, control, cost reduction etc.), it’s important to realize that cloud environments are vulnerable to both inside and outside attacks.
Most cloud service providers offer airtight cloud storage security. It’s how cloud storage services are used that presents a risk to many organizations. Recent research has revealed huge volumes of publicly-accessible storage, huge volumes of unencrypted data, and an increasing number of data breaches attributable to compromised credentials.
In this article we’ll discuss cloud storage security best practices.

Cloud storage security
Cloud security—also referred to as cloud computing security—is designed to protect cloud environments from unauthorized use/access, distributed denial of service (DDoS) attacks, hackers, malware, and other risks. To accomplish this, cloud security uses strategy, policies, processes, best practice, and technology.
Cloud data security typically involves a number of tools, technologies and approaches. A major advantage to the cloud is that many security elements are already built into systems. This typically includes strong encryption at rest and in motion. It may also involve:
- Geo-fencing. The use of IP addresses and other geolocation data to create a geographic boundary and identify suspicious activity.
- Policy-based lifecycle retention. Systems use data classification polices to manage and automate how data is stored, retained, archived and deleted.
- Data-aware filtering. This function allows organizations to watch for specific conditions and events – and who has accessed information and when they accessed it. It can be tied to role-based authorizations and privileges.
- Detailed logs and full user/workload audit trail reporting. The ability to peer into logs and audit workloads can provide insight into security concerns and vulnerability risks.
- Backup and recovery functions. These essential capabilities allow an organization to navigate an outage but also deal with security risks such as ransomware attacks and maliciously deleted data. Robust cloud-based disaster recovery solutions leads to availability across all conditions.
In March 2018, Gartner predicted “through 2022, at least 95 percent of cloud security failures will be the customer’s fault”. Although not specifically focusing on cloud storage security, there is little doubt Gartner had this in mind when suggesting businesses should develop a strategy that “includes guidance on what data can be placed into which clouds under what circumstances”.
Cloud security is tight, but it’s not infallible. Cybercriminals can get into those files, whether by guessing security questions or bypassing passwords.
But the bigger risk with cloud storage is privacy. Even if data isn’t stolen or published, it can still be viewed. Governments can legally request information stored in the cloud, and it’s up to the cloud services provider to deny access. Tens of thousands of requests for user data are sent to Google, Microsoft, and other businesses each year by government agencies. A large percentage of the time, these companies hand over at least some kind of data, even if it’s not the content in full.
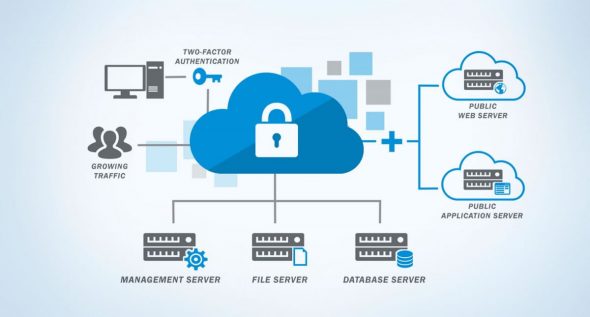
Cloud storage security best practices
Before committing to a cloud based storage architecture, discuss the physical security features that your provider has implemented. Ask questions that detail how hardened their access policies are for getting onsite. Keep in mind, securing your data is a partnership between you and the provider. Typical security measures such as firewalls, VLANs and multi factor authentication should be implemented.
First, understand the flow of data for each application. Once you understand the correlation of data to application, you can then implement several key policies that will safeguard your data. Role Based Access is a key step in securing your data and environment. Limiting users to access only the necessary applications and data essential to their job function in essence limits the reach of a rogue employee.
Access management generally requires three capabilities: the ability to identify and authenticate users, the ability to assign users access rights, and the ability to create and enforce access control policies for resources.
It’s impossible to monitor cloud storage security best practices when you may have millions of assets deployed in the cloud. So, an ideal solution is to implement a cloud management platform with automation capabilities that can monitor compliance with governance policies and alert system administrators to policies violations, or take an administrator-defined action to prevent a breach of cloud storage security.
To govern your cloud with automation, all you need to do is define the policies users must comply with and the actions you require the cloud management platform to take if a policy violation occurs. The solution then monitors cloud activity around the clock, alerting you to activities that may compromise your business’s cloud storage security. Example policies could include:
- If any CloudTrail S3 bucket is publicly accessible, restrict access and send email notification.
- If any S3 bucket with tag “PII” is unencrypted, execute function to encrypt bucket.
- If an IAM User’s Cloud Access Key has not been rotated in 90 days, send an email notification.
- If any privileged IAM user has MFA disabled, execute function to revoke access.
Conclusion
Most cloud service providers offer airtight cloud storage security. It’s how cloud storage services are used that presents a risk to many organizations.
If you have any questions about how we can help you optimize your cloud costs and performance, contact us today to help you out with your performance and security needs.






