Sign up to our Newsletter
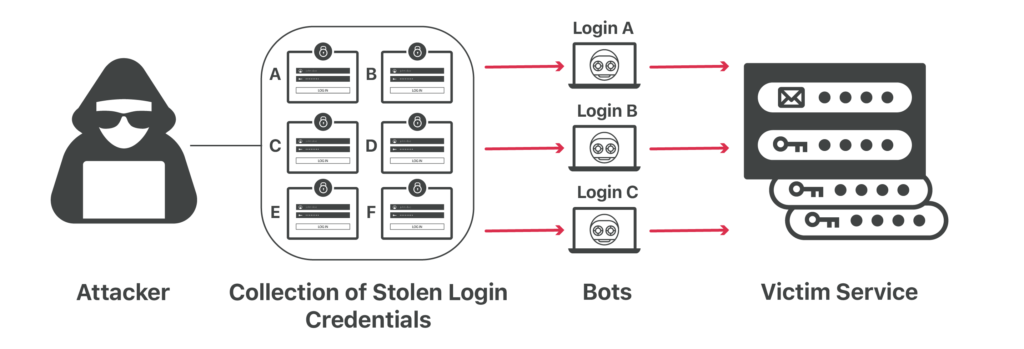
Credential stuffing is a type of cyberattack where stolen account credentials typically consisting of lists of usernames and/or email addresses and the corresponding passwords (often from a data breach) are used to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application.
According to OWASP, credential stuffing is the automated injection of breached username/password pairs in order to fraudulently gain access to user accounts. This is a subset of the brute force attack category: large numbers of spilled credentials are automatically entered into websites until they are potentially matched to an existing account, which the attacker can then hijack for their own purposes.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Unlike credential cracking, credential stuffing attacks do not attempt to brute force or guess any passwords – the attacker simply automates the logins for thousands to millions of previously discovered credential pairs using standard web automation tools like Selenium, cURL, PhantomJS or tools designed specifically for these types of attacks such as: Sentry MBA, SNIPR, STORM, Blackbullet and Openbullet.
Credential stuffing attacks are possible because many users reuse the same username/password combination across multiple sites, with one survey reporting that 81% of users have reused a password across two or more sites and 25% of users use the same password across a majority of their accounts.
How credential stuffing attacks work
Credential stuffing is a cyberattack in which credentials obtained from a data breach on one service are used to attempt to log in to another unrelated service.
Credential stuffing attacks are launched through botnets and automated tools that support the use of proxies that distribute the rogue requests across different IP addresses. Furthermore, attackers often configure their tools to mimic legitimate user agents — the headers that identify the browsers and operating systems web request are made from.
Over a 17-month period, from November 2017 through the end of March 2019, security and content delivery company Akamai detected 55 billion credential stuffing attacks across dozens of verticals. While some industries were more heavily targeted than others — for example gaming, retail and media streaming — no industry was immune.
The Ponemon Institute’s Cost of Credential Stuffing report found that businesses lose an average of $4 million per year to credential stuffing. These losses take the form of application downtime, lost customers, and increased IT costs. Large-scale botnet attacks can overwhelm a business’ IT infrastructure, with websites experiencing as much as 180 times their typical traffic during an attack.
And despite the uptick in reported attacks, it’s safe to assume that many businesses do not disclose when their systems are compromised, and their internal data is stolen, so we may never know the full cost.
Detecting and preventing credential stuffing attacks
Detecting bots requires identifying whether the sender of a request is a human or not. Simple bot detection techniques examine the content of a request, such as by looking at the header. However, this approach is not reliable against more sophisticated bots, because request headers are easily spoofed. More advanced bot detection techniques use JavaScript challenges, browser fingerprinting, and behavior anomaly analysis.
There are multiple ways to try to detect a credential stuffing attack.
- Monitor for abnormal amount of login attempts to an account from a single endpoint.
- Monitor access attempts to multiple accounts from a single endpoint.
- Detecting known malicious endpoints attempting to use the credential via their IP address or fingerprinting techniques.
- Detecting the use of automation software in the login process.
- Remove credentials based login and replace with passwordless authentication.
How users can protect themselves
Here are some recommendations for individual users about how they can protect themselves:
- Avoid reusing passwords: Use a unique password for each account you use online. That way, even if your password leaks, it can’t be used to sign in to other websites. Attackers can try to stuff your credentials into other login forms, but they won’t work.
- Use a password manager: Remembering strong unique passwords is a nearly impossible task if you have accounts on quite a few websites, and almost everyone does. We recommend using a password manager like 1Password (paid) or Bitwarden (free and open-source) to remember your passwords for you. It can even generate those strong passwords from scratch.
- Enable two-factor authentication: With two-step authentication, you have to provide something else—like a code generated by an app or sent to you via SMS—each time you log in to a website. Even if an attacker has your username and password, they won’t be able to sign in to your account if they don’t have that code.
- Get leaked password notifications: With a service like Have I Been Pwned?, you can get a notification when your credentials appear in a leak.
How companies can protect themselves against credential stuffing
Use multi-factor authentication
Multi-factor authentication (MFA) is by far the best defense against the majority of password-related attacks, including credential stuffing and password spraying. As such, it should be implemented wherever possible; however, depending on the audience of the application, it may not be practical or feasible to enforce the use of MFA.
IP Blacklisting
Attackers will typically have a limited pool of IP addresses, so another effective defense is to block or sandbox IPs that attempt to log into multiple accounts. You can monitor the last several IPs that were used to log into a specific account and compare them to the suspected bad IP, to reduce false positives.
Flag unrecognized devices
A credential stuffing attack attack will most often come from a new, unrecognized device, so your team can help prevent attacks by keeping an eye on the devices attempting to access your accounts. You should always check IP addresses to ascertain whether the device the request originates from is one your team has seen before. Organizations can use cookies to save approved logins and validate the device in the future. Then, if the login is coming from an unrecognized location, additional steps should be taken to verify the user.
Use CAPTCHA
Requiring a user to solve a CAPTCHA for each login attempt can help to prevent automated login attempts, which would significantly slow down a credential stuffing or password spraying attack. However, CAPTCHAs are not perfect, and in many cases tools exist that can be used to break them with a reasonably high success rate.
To improve usability, it may be desirable to only require the user solve a CAPTCHA when the login request is considered suspicious.
Align Website Architecture with Different Types of Clients
If achieving the smallest possible attack surface is your goal, then the ideal solution has to align the website architecture with different types of clients. Some organizations have already done this to varying degrees.
Others may need to rearchitect their website in order to do so. Breaking existing endpoints into separate URLs helps reduce the attack surface by providing the most granular control of transactional URL traffic.
For example, you might segment your clients by URL as follows:
- URL 1: Humans on desktop, laptop, and mobile browsers
- URL 2: Native mobile apps
- URL 3: Automated third-party services, such as industry aggregators and partners
With this approach, you will be able to apply the appropriate bot detection to URL 1 and URL 2, and force other types of consumers to URL 3. While you can’t use behavioral anomaly bot detection to protect URL 3, you can control the data and application features available to its users.
Conclusion
Credential stuffing attacks pose a significant cyber threat not only for individuals, but also for companies.
If you have any questions about how we can help you protect your website and business from cyber-attacks, contact us today to help you out with your performance and security needs.






