Sign up to our Newsletter
Online fraud is destroying customer trust and corroding revenue. Data from the Federal Trade Commission show the full extent of today’s problem: fraud losses in the US rose to $5.9 billion in 2021, an increase of 436% from 2017. Further research conducted by PWC shows that it’s not just individuals being duped by these global criminal rings – more than half of companies counting at least $10 billion in yearly revenue have experienced a successful fraudulent attack within the last year. Bot-based protection is getting outdated, and user-experience-draining mitigation is lethal to conversion rates.
Thanks to our partnership with Cloudflare, we are now able to offer new, innovative fraud detection tools that will help your organization better handle fraudulent activity – putting both customer protection and experience first.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Oldschool Fraud Prevention Misses its Mark
Online fraudulent behavior can take several different forms: even something as apparently mundane as fake account creation can be utilized in complex and extended attacks. One user accessing, or wielding, the resources of many can be a major contributing feature to poor performance for genuine site visitors, which holds a direct causational relationship with a site’s revenue generation.
More directly threatening to an organization, and its customers, than slow loading times is the risk of account takeover. Either by abusing account recovery methods, or utilizing stolen password and email combinations, account takeover attacks pave the way for malicious behavior with a far-reaching blast radius. This is amplified by today’s propensity for employees and end-users alike to reuse passwords. For instance, if an account is hacked, it then becomes possible for an attacker to access and use any pre-saved card details. These fraudulent transactions are yet another risk for businesses: both devaluing the brand image and reputation while actively harming your loyal customers, the projected value of payment card fraud by 2027 looks to be $38.5 billion USD.
Organizations that allow fraudulent card transactions also become honeypots and havens for further criminal activity, as the payment process is swiftly used as a testing ground for recently-stolen card details.
The final – and perhaps newest – form of online fraud comes in the form of expediting. This sees malicious actors circumventing the normal and expected user flow – in order to skip queues, bulk-buy in-demand items, and complete orders faster than should be possible.
Anti-bot teams are already very familiar with the growing presence of online fraud. Some of the most established forms of malicious activity online have seen the automation of all of the above – profiteering cybercriminals can leverage thousands of automated bot actors in order to conduct widespread attacks.
While the cutting-edge bot protection provided to GlobalDots customers is a vital tool in fraud prevention, modern cybercriminals are well-versed in the limitations of bot activity. This is why, for high-value targets, attackers regularly contract out some of the more human labor. When a target holds significant value, malicious actors often outsource the exploitation of online applications to actual individuals. To enhance the security of online applications and combat contemporary online fraud, security teams must consider factors beyond merely bots.
Prevention at the Cost of User Experience
Traditional prevention mechanisms present organizations with a stark choice: protect end-users at the cost of their online experience or leave both completely unprotected. A sense of frustration underlies many of the teams aiming to combat online fraud; after all, there are technically solutions available.
Many of the typical anti-fraud measures enforced look familiar: requiring email verification when users first sign up, enforcing multi-factor authentication for every single login, and blocking online purchases from anonymizing VPNs and countries regularly associated with higher numbers of chargebacks. While these seem like good approaches on the surface, deeper research has found that support teams and customers are left in a lose-lose situation.
While these measures would undeniably cut down on fraudulent activity, they would also deeply depress the revenue streams from a site. Not only is the customer forced to sit through increasingly draconic levels of authentication and anti-fraud measures – increasing the bounce rate across the board – but there’s also the ongoing issue of legitimate transactions being denied. One study discovered that up to two thirds of declined transactions are, in fact, legitimate.
Faced with the severe impacts on user experience, many companies have made the tough choice to simply swallow the cost of online fraud. For those who’ve chosen to bear the brunt of fraud in an attempt to provide frictionless user experience, the operational outcomes have hit hard.
These organizations have faced troubles of their own, battling higher infrastructural costs and inefficiency within its employees. The modus operandi of threat actors have widespread implications. For instance, it’s common for bad actors to abuse account creation endpoints with floods of HTTP requests. These often occur in highly distributed waves, bypassing IP-based limiters. This renders basic protection blind: with no way to distinguish between genuine and malicious site visitors, an organization must simply assume all are legitimate. This leads to infrastructure scale-ups to serve these higher peaks in request traffic. This leveled-up infrastructure comes with its own demands on the organization, including financial impacts. Engineering teams are suddenly faced with entirely new responsibilities, such as sinking time into banning IP addresses (that may never be used again); wiping fraudulent data from at-capacity databases; and sometimes personally bearing the burden of investigating users’ fraud disputes.
Ultimately, online fraud has left organizations in a more inefficient and less user-friendly bind – no matter what choice they’ve made.
Modern Protection with GlobalDots
As Cloudflare’s largest value-added-reseller in EMEA, GlobalDots champions cloud innovation by connecting over 1,000 global organizations with the latest cloud, security, and web performance technologies, offering them discounted pricing.
This new form of protection utilizes the scale and threat intelligence provided to so many global companies: with 45 million HTTP requests being monitored per second, the huge diversity of traffic allows a unique opportunity for analyzing and eradicating online fraud.
For instance, by modeling account attack data, it becomes possible to analyze the patterns in signup submission data. The data provided by this threat intelligence allows for preliminary identification of 72% of fake accounts; these are identified via signup details such as certain email addresses and the domain being used in the attacks. With higher numbers of threat-intelligence based rules, this number is now closing in on 100%. Machine learning models are also being fed this data, allowing for further innovation in identifying the patterns of fake account creation.
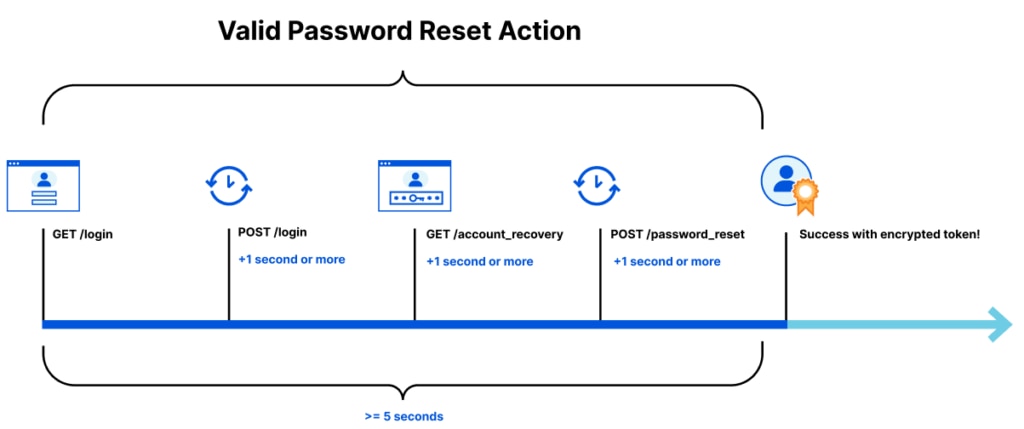
A second newly-created technique works to directly combat expediting attacks. Forcing attackers to wait their turn can combat much of the profit-driven industry, and is achieved via a single background check on the user themselves. Take the example of an account recovery page that’s being spammed by sophisticated threat actors stealing reset tokens. Legitimate email addresses are being used, and they would like this process to be as fast as possible. In order to complete a password reset, a user normally has to make a string of requests: a GET to render the login site (and a POST immediately after); a GET for account recovery; and POST to the password reset page. Each of these are performed in quick succession, taking a total time of less than 5 seconds. This legitimate process can be neatly defined via a token. By assembling the encrypted data, it becomes possible to check that the user has made every step in its correct order – and at roughly the right point in time.
This token becomes a VIP pass for authorized users, forcing bad actors to behave the same as a legitimate visitor. This makes the process of checking which compromised email addresses may be registered an impossibly slow process, forcing them to move on to a different target.
To discuss more of the web security innovations that help protect brands such as Bosch, Payoneer and Lufthansa, get in touch today. As attackers further evolve and shift, GlobalDots will continue to provide cutting-edge innovation, placing customer experience and protection front-and-center.






