Sign up to our Newsletter
In this guide we will examine the most common types of DDoS attacks, how they are performed and how they can be prevented.
Denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
In a distributed denial-of-service (DDoS) attack, the incoming traffic flooding the victim originates from many different sources. This effectively makes it impossible to stop the attack simply by blocking a single source.
The hack is done through the master computer system that communicates with, sometimes as many as hundreds of thousands, controlled end user machines. These machines, known as zombies or bots, follow the instruction from the master system and massively launch packets at the targeted site to overwhelm the targeted machine and stop it from functioning.
The usual targets for DoS or DDoS attacks typically include websites hosted on high-profile web servers (such as credit card payment gateways, banks, government bodies) and most commonly, the target machine is so overwhelmed with external communication requests that it can either respond too slow, or not at all, and is considered effectively – unavailable.
Even if such denial-of-service occurs for only a few hours, it almost always implies a significant loss of revenue for the targeted host.
DoS and DDoS attacks present a major challenge for businesses, and even governments, since they can bring websites down and make information unavailable for users.
The United States Computer Emergency Readiness Team (US-CERT) has identified symptoms of a denial-of-service attack to include:
- unusually slow network performance (opening files or accessing web sites)
- unavailability of a particular web site
- inability to access any web site
- dramatic increase in the number of spam emails received (this type of DoS attack is considered an e-mail bomb).
Attack possibilities by OSI layer
DDoS attacks can target one of the seven OSI layers. Open Systems Interconnection (OSI) model is a conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology.
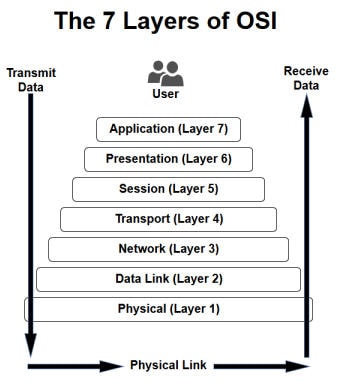
Let’s examine DDoS attacks by each layer.
Application Layer (7)
A Layer 7 DDoS attack is an attack structured to overload specific elements of an application server infrastructure.
Layer 7 attacks are especially complex, stealthy, and difficult to detect because they resemble legitimate website traffic. Even simple Layer 7 attacks–for example those targeting login pages with random user IDs and passwords, or repetitive random searches on dynamic websites–can critically overload CPUs and databases. Also, DDoS attackers can randomize or repeatedly change the signatures of a Layer 7 attack, making it more difficult to detect and mitigate.
Examples of DoS techniques:
- PDF GET requests,
- HTTP GET,
- HTTP POST, = website forms
(login, uploading photo/video,
submitting feedback)
Potential impact of DoS attack:
- Reach resource limits of
services - Resource starvation
Mitigation options
Application monitoring is the practice of monitoring software applications using a dedicated set of algorithms, technologies, and approaches to detect zero day and application layer (Layer 7 attacks). Once identified these attacks can be stopped and traced back to a specific source more easily than other types of DDoS attacks.
Presentation Layer (6)
Examples of DoS techniques:
- Malformed SSL Requests — Inspecting SSL encryption packets is resource intensive. Attackers use SSL to tunnel HTTP attacks to target the server.
Potential impact of DoS attack:
- The affected systems could stop accepting SSL connections or automatically restart.
Mitigation options
To mitigate, consider options like offloading the SSL from the origin infrastructure and inspecting the application traffic for signs of attacks traffic or violations of policy at an applications delivery platform (ADP).
A good ADP will also ensure that your traffic is then re-encrypted and forwarded back to the origin infrastructure with unencrypted content only ever residing in protected memory on a secure bastion host.
Session Layer (5)
Examples of DoS techniques:
- Telnet DDoS-attacker exploits a flaw in a Telnet server software running on the switch, rendering Telnet services unavailable.
Potential impact of DoS attack:
- Prevents administrator from performing switch management functions.
Mitigation options
Check with your hardware provider to determine if there’s a version update or patch to mitigate the vulnerability.
Transport Layer (4)
Layer 3 and Layer 4 DDoS attacks are types of volumetric DDoS attacks on a network infrastructure. Layer 3 (network layer) and 4 (transport layer) DDoS attacks rely on extremely high volumes (floods) of data to slow down web server performance, consume bandwidth, and eventually degrade access for legitimate users.
These attack types typically include ICMP, SYN, and UDP floods.
Examples of DoS techniques:
- SYN flood
- Smurf attack
Potential impact of DoS attack:
- Reach bandwidth or connection limits of hosts or networking equipment.
Mitigation options
DDoS attack blocking, commonly referred to as blackholing, is a method typically used by ISPs to stop a DDoS attack on one of its customers. This approach to block DDoS attacks makes the site in question completely inaccessible to all traffic, both malicious attack traffic and legitimate user traffic.
Black holding is typically deployed by the ISP to protect other customers on its network from the adverse effects of DDoS attacks such as slow network performance and disrupted service.
Network Layer (3)
Examples of DoS techniques:
- ICMP Flooding – A Layer 3 infrastructure DDoS attack method that uses ICMP messages to overload the targeted network’s bandwidth
Potential impact of DoS attack:
- Can affect available network bandwidth and impose extra load on the firewall
Mitigation options
Rate-limit ICMP traffic and prevent the attack from impacting bandwidth and firewall performance.
Data Link Layer (2)
Examples of DoS techniques:
- MAC flooding — inundates the network switch with data packets
Potential impact of DoS attack:
- Disrupts the usual sender to recipient flow of data — blasting across all ports
Mitigation options
Many advances switches can be configured to limit the number of MAC addresses that can be learned on ports connected to end stations; allow discovered MAC addresses to be authenticated against an authentication, authorization and accounting (AAA) server and subsequently filtered.
Physical Layer (1)
Examples of DoS techniques:
- Physical destruction, obstruction, manipulation, or malfunction of physical assets.
Potential impact of DoS attack:
- Physical assets will become unresponsive and may need to be repaired to increase availability.
Mitigation options
Practice defense in-depth tactics, use access controls, accountability, and auditing to track and control physical assets.
Possible DDoS traffic types
HTTP Header
HTTP headers are fields which describe which resources are requested, such as URL, a form, JPEG, etc. They also inform the web server what kind of web browser is being used.
Common HTTP headers are GET, POST, ACCEPT, LANGUAGE, and USER AGENT. The requester can insert as many headers as they want and can make them communication specific. DDoS attackers can change these and many other HTTP headers to make it more difficult to identify the attack origin.
In addition, HTTP headers can be designed to manipulate caching and proxy services. For example, is it possible to ask a caching proxy to not cache the information.
SYN Flood (TCP/SYN)
SYN Flood works by establishing half-open connections to a node. When the target receives a SYN packet to an open port, the target will respond with a SYN-ACK and try to establish a connection.
However, during a SYN flood, the three-way handshake never completes because the client never responds to the server’s SYN-ACK. As a result, these “connections” remain in the half-open state until they time out.
UDP Flood
UDP floods are used frequently for larger bandwidth DDoS attacks because they are connectionless and it is easy to generate protocol 17 (UDP) messages from many different scripting and compiled languages.
ICMP Flood
Internet Control Message Protocol (ICMP) is primarily used for error messaging and typically does not exchange data between systems. ICMP packets may accompany TCP packets when connecting to a sever.
An ICMP flood is a layer 3 infrastructure DDoS attack method that uses ICMP messages to overload the targeted network’s bandwidth.
MAC Flood
A rare attack, in which the attacker sends multiple dummy Ethernet frames, each with a different MAC address, Network switches treat MAC addresses separately, and hence reserve some resources for each request. When all the memory in a switch is used up, it either shuts down or becomes unresponsive.
In a few types of routers, a MAC flood attack may cause these to drop their entire routing table, thus disrupting the whole network under its routing domain.
Mitigating large scale DoS/DDoS attacks
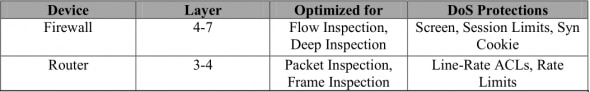
Some DDoS mitigation actions and hardware:
- Stateful inspection firewalls
- Stateful SYN Proxy Mechanisms
- Limiting the number of SYNs per second per IP
- Limiting the number of SYNs per second per destination IP
- Set ICMP flood SCREEN settings (thresholds) in the firewall
- Set UDP flood SCREEN settings (thresholds) in the firewall
- Rate limit routers adjacent to the firewall and network
The good news
Although DDoS are becoming more complex and pervasive each year, businesses can mitigate their effects by utilizing a cloud-based DDoS protection service.
By combining the most intelligent DDoS mitigation tools on the planet with an unparalleled monitoring and support apparatus, GlobalDots can eliminate these threats before you and your customers even realize that they’re there.
GlobalDots can help you protect your business from DDoS attacks of any size and intensity. Even with the most complex and sophisticated setups, GlobalDots can provide you with the technology stack that ensures that the most important aspects of your site are always up & running: deliverability, speed, availability, failover and web security (including web application protection, bot protection, DDoS protection and mitigation).
Customers like Lufthansa, Playtika, Trading View, Lamborghini, Bosch, Fiat, Rocket Internet, Benetton, Bulova and other leading brands and small-medium enterprises rely on GlobalDots services to keep their sites and applications fast & secure. Contact us today to help you out with your performance and security needs.






