Sign up to our Newsletter
As threats of DDoS attacks continue to increase, enterprises of all sizes are looking for ways to amp up their protection and mitigation techniques.
DDoS attacks have the ability to disrupt and shut down enterprise systems, so companies are really putting a lot of resources into stopping them. Organizations are countering DDoS attacks in a number of different ways, from different angles, to secure networks against failure and damage.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

One of the ways that companies are mitigating DDoS attacks is with added capacity. The arrival of cloud services means companies are much more able to order on-demand server capacity. This helps with peak traffic times, and it can help with DDoS attacks too. By having more overhead capacity, the business network is able to better stand up to the beginning of a DDoS attack as it grows.
Other DDoS attack mitigation strategies have to do with limiting the influence of the traffic that may be involved in these attacks.
In this article we discuss DDoS attacks and 3 steps to better DDoS protection you can implement right now.
How DDoS attacks work
A DDoS attack starts with a botnet, which is essentially a group of computers that have been infected with malware and can be controlled as one entity by an outside party. These are private computers that have been hacked without the user’s knowledge and can then be used to attack networks or services in a variety of ways. For example, one DDoS attack might use spam messages to overwhelm an email service and cause issues, while another may use those computers to send fake traffic to a service such as Twitter and temporarily bring it down.
The interesting thing about botnets is that they are widely available on the black market for a range of prices and a variety of use cases. For example, for $200 to $500 you can buy a turnkey botnet with maybe 50 “zombies,” which is the term for the infected computers. For varying fees, you can rent larger botnets with thousands of bots by the hour. The goal of the attack, as well as the target, will determine what type of botnet needs to be used and for how long.
DDoS attacks vary in method and presentation. While some DDoS attacks are designed to saturate bandwidth and infrastructure, other categories of DDoS include session-based attacks, simulation replay and amplification. Attackers are using amplification to dramatically increase the traffic volume received by the target, and to deplete the target’s resources more quickly. These attacks use Domain Name Server (DNS) spoofed requests and public recursive servers, leveraging innocent bystanders as well as bots.
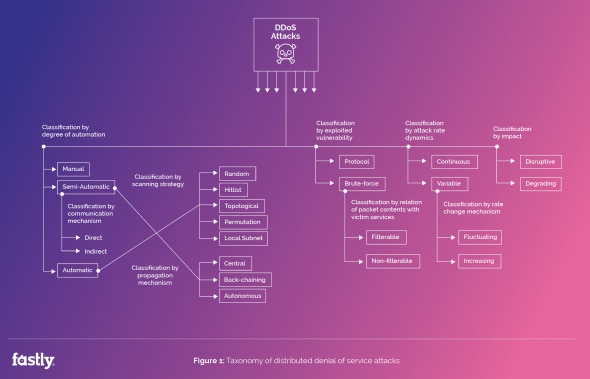
One of the newer developments in DDoS (distributed denial of service) attacks is using Internet of Things devices in place of computers. In the same way that an attacker would create a private network of infected computers to perpetrate attacks and send unwanted traffic to networks and services, hackers are now taking advantage of a 12-year-old vulnerability in the SSH protocols of IoT devices to use them for DDoS purposes. What’s happening is these IoT devices are shipped with this vulnerability in their credentials, which are often used for remotely logging in to computer systems and accounts, and if they aren’t changed immediately after purchase, then hackers can take advantage of the flaw and take over the device.
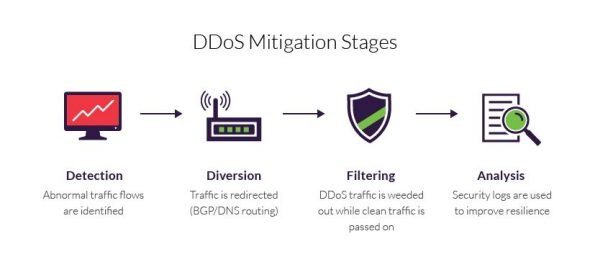
The mitigation process stages
A typical mitigation process can be broadly defined by these four stages:
- Detection – The identification of traffic flow deviations that may signal the buildup of a DDoS assault. Effectiveness is measured by your ability to recognize an attack as early as possible, with instantaneous detection being the ultimate goal.
- Diversion – Traffic is rerouted away from its target, either to be filtered or completely discarded.
- Filtering – DDoS traffic is weeded out, usually by identifying patterns that instantly distinguish between legitimate traffic (i.e., humans, API calls and search engine bots) and malicious visitors. Responsiveness is a function of your being able to block an attack without interfering with your users’ experience. The aim is for your solution to be completely transparent to site visitors.
- Analysis – Security logs are reviewed to gather information about the attack, both to identify the offender(s) and to improve future resilience. The process’s effectiveness relies on the existence of detailed security logs that can offer granular visibility into the attack traffic.
Steps to better DDoS Protection
1. Identify what you need to protect and the business impact of its loss
Every organization’s needs are different. What Internet-facing assets do you need to protect from DDoS attacks? If you didn’t protect them and they became unavailable, what business impact and costs would you incur, including operational, financial, regulatory and reputation costs?
- Do you only care to protect your website? Web applications? APIs?
- How about your origin server? DNS servers?
- Can a business case be made to protect your data center and network infrastructure?
Knowing what you need to protect will affect the type of DDoS protection. Not all attacks target ports 80 and 443.
- Protecting a data center, network infrastructure and other non-website assets such as email servers requires a DDoS scrubbing network.
- A content delivery network (CDN) with DDoS mitigation and web application firewall capabilities can protect web assets, including websites, web applications, and APIs. A CDN can also protect origin servers, and primary and secondary DNS infrastructure.
2. Deploy a DDoS protection service before you need it
Select a DDoS protection service before you need it. Avoiding the chaos, delays and panic of looking for DDoS protection when under attack has several additional advantages:
- Have time to choose the best solution. Your DDoS protection provider can explain the approaches to DDoS protection that would meet your specific needs. They can look for gaps to ensure you are fully protected.
- Know who to call and what to do. Develop a relationship with your DDoS protection provider and know what to do and whom to call when under attack.
- Get ready for DDoS protection. Lay the groundwork and set up your DDoS protection service. For example, setting DNS time-to-live (TTL) to a short duration will speed time to mitigation when routing traffic to a scrubbing service.
- Test and optimize: Work with your DDoS protection provider to test and validate your DDoS scrubbing service. Test the process, ensure that your applications continue to work as expected, and optimize settings.
3. Develop a DDoS response playbook
A DDoS response playbook allows your organization to experience a controlled, streamlined response to a DDoS attack.
- If you choose on-demand mitigation with manual activation, your organization needs to know what to look for, what to do, and whom to call in order to activate the DDoS service.
- If you have an always-on or automatically triggered DDoS protection service, your organization needs to know how to respond if hit by a zero-day attack or a DDoS attack that targets an unanticipated failure point for which your organization is unprotected.
A DDoS response playbook should include incident response processes, escalation paths, and points of contact.
Conclusion
DDoS attacks have the ability to disrupt and shut down enterprise systems, so companies are really putting a lot of resources into stopping them. If you need help with DDoS protection and mitigation, contact us today to help you out with all your performance and security needs.






